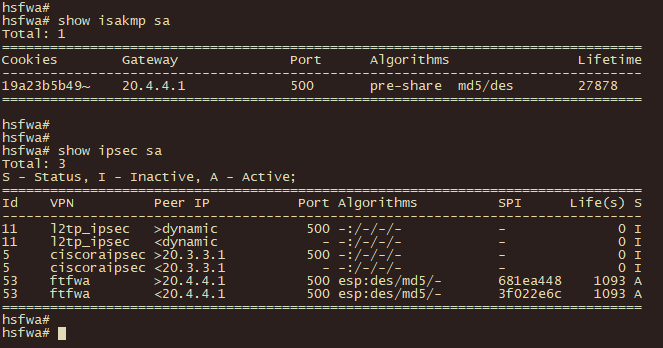
需求:企业新分支机构E部署飞塔防火墙为互联网出口网关,需与总部hillstonefwa建立ipsec vpn。
山石防火墙配置
hsfwa# show configuration
zone “untrust”
type wan
exit
zone “ipsecvpn“
vrouter “trust-vr”
exit
hostname “hsfwa”
isakmp proposal “ftfwa“
hash md5
encryption des
exit
isakmp peer “ftfwa“
mode aggressive
isakmp-proposal “ftfwa“
pre-share “123456“
peer 20.4.4.1
nat-traversal
interface ethernet0/1
exit
ipsec proposal “ftfwa“
hash md5
encryption des
group 2
exit
tunnel ipsec “ftfwa” auto sa-index 53
isakmp-peer “ftfwa“
ipsec-proposal “ftfwa“
auto-connect
id local 10.1.1.0/24 remote 172.16.4.0/24 service “any”
exit
interface ethernet0/0
zone “trust”
ip address 10.1.1.254 255.255.255.0
manage ping
manage ssh
exit
interface ethernet0/1
zone “untrust”
ip address 20.0.0.1 255.255.255.0
manage ping
exit
interface tunnel60
zone “ipsecvpn“
manage ping
tunnel ipsec “ftfwa“
reverse-route prefer
exit
ip vrouter “trust-vr”
snatrule id 1 from “10.1.1.0/24” to “Any” service “Any” eif ethernet0/1 trans-to eif-ip mode dynamicport
ip route 0.0.0.0/0 20.0.0.100
ip route 172.16.4.0/24 “tunnel60“
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 61
action permit
src-zone “trust”
dst-zone “ipsecvpn“
src-ip 10.1.1.0/24
dst-ip 172.16.4.0/24
service “Any”
exit
rule id 62
action permit
src-zone “ipsecvpn“
dst-zone “trust”
src-ip 20.4.4.1/32
src-ip 172.16.4.0/24
dst-ip 10.1.1.0/24
service “Any”
exit
End飞塔防火墙配置
ftfwa # show
config system global
set hostname “ftfwa“
end
config system interface
edit “port1”
set vdom “root”
set ip 172.16.4.254 255.255.255.0
set allowaccess ping ssh
next
edit “port2”
set vdom “root”
set ip 20.4.4.1 255.255.255.0
set allowaccess ping
next
end
config firewall address
edit “localvpn“
set subnet 172.16.4.0 255.255.255.0
next
edit “remotevpn“
set subnet 10.1.1.0 255.255.255.0
next
end
config vpn ipsec phase1
edit “hsfwa“
set interface “port2”
set dhgrp 2
set mode aggressive
set proposal des-md5
set remote-gw 20.0.0.1
set psksecret 123456
next
end
config vpn ipsec phase2
edit “hsfwap2“
set phase1name “hsfwa“
set proposal des-md5
set keepalive enable
set auto-negotiate enable
set dhgrp 2
set src-subnet 172.16.4.0 255.255.255.0
set dst-subnet 10.1.1.0 255.255.255.0
next
end
config firewall policy
edit 10
set srcintf “port1”
set dstintf “port2”
set srcaddr “all”
set dstaddr “all”
set action accept
set schedule “always”
set service “ALL”
set nat enable
next
edit 60
set srcintf “port1”
set dstintf “port2”
set srcaddr “localvpn“
set dstaddr “remotevpn“
set action ipsec
set schedule “always”
set service “ALL”
set inbound enable
set outbound enable
set vpntunnel “hsfwa“
next
move 60 before 10
end测试验证:
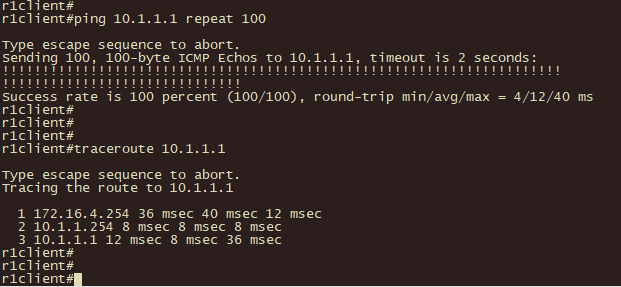
1、分支机构客户使用ping 和 traceroute 验证至总部服务器的连通性和路径;
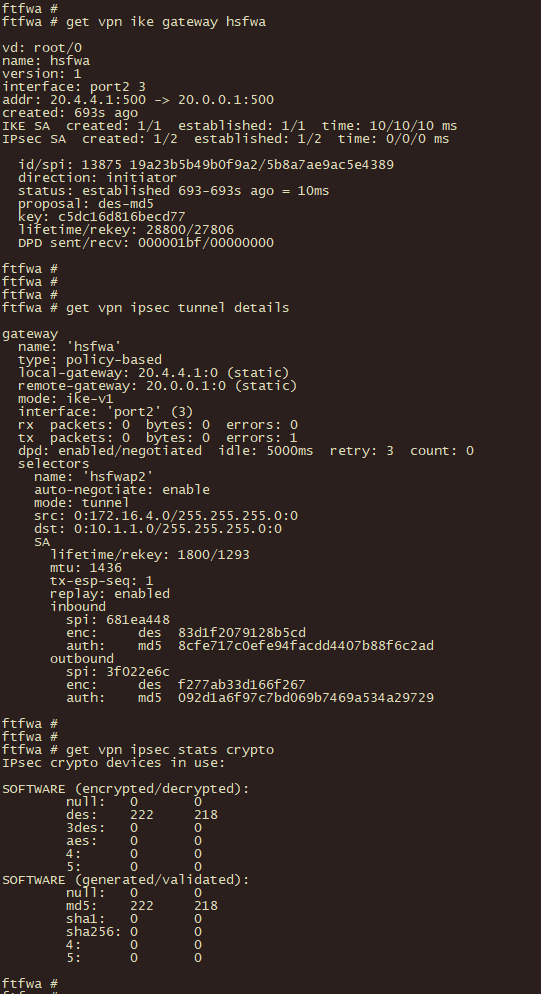
2、分支机构飞塔防火墙使用以下命令验证 ipsec vpn 第一阶段、第二阶段协商状态及数据包加密状态
get vpn ike gateway
get vpn ipsec tunnle details
get vpn ipsec stats crypto
3、总部山石头防火墙使用以下命令验证 show isakmp sa 和 show ipsec sa 查看验证IPSEC VPN 第一阶段、第二阶段协商状态