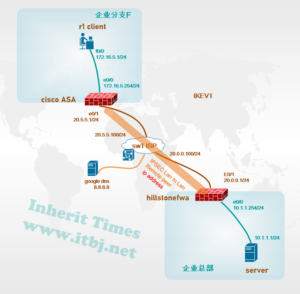
需求:企业新分支机构F部署CISCO ASA 做为互联网出口网关,与总部山石防火墙建立IPSEC VPN 以实现资源共享
分支机构F的CISCO ASA 软件版本为8.2 ,支持 IKE verison V1。
山石防火墙与思科ASA IPSEC VPN IKEV1 配置如下:
hsfwa# show configuration
zone “ipsecvpn“
vrouter “trust-vr”
exit
hostname “hsfwa”
isakmp proposal “psk-md5-3des-g2“
hash md5
exit
isakmp peer “ciscoasa“
mode aggressive
isakmp-proposal “psk-md5-3des-g2“
pre-share “123456“
peer 20.5.5.1
nat-traversal
accept-all-peer-id
interface ethernet0/1
exit
ipsec proposal “esp-md5-3des-g2“
hash md5
encryption 3des
group 2
exit
tunnel ipsec “ciscoasa” auto
isakmp-peer “ciscoasa“
ipsec-proposal “esp-md5-3des-g2“
auto-connect
id local 10.1.1.0/24 remote 172.16.5.0/24 service “any”
exit
interface ethernet0/0
zone “trust”
ip address 10.1.1.254 255.255.255.0
manage ssh
exit
interface ethernet0/1
zone “untrust”
ip address 20.0.0.1 255.255.255.0
manage ping
exit
interface tunnel70
zone “ipsecvpn“
manage ping
tunnel ipsec “ciscoasa“
reverse-route prefer
exit
ip vrouter “trust-vr”
snatrule id 1 from “10.1.1.0/24” to “Any” service “Any” trans-to eif-ip mode dynamicport
ip route 0.0.0.0/0 20.0.0.100
ip route 172.16.5.0/24 “tunnel70“
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 71
action permit
src-zone “trust”
dst-zone “ipsecvpn”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 72
action permit
src-zone “ipsecvpn”
dst-zone “trust”
src-addr “Any”
dst-ip 10.1.1.0/24
service “Any”
exit
Endciscoasa# show run
ASA Version 8.2(1)
!
hostname ciscoasa
!
interface Vlan10
nameif inside
security-level 100
ip address 172.16.5.254 255.255.255.0
!
interface Vlan20
nameif outside
security-level 0
ip address 20.5.5.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
switchport access vlan 20
!
access-list ipsecvpn extended permit ip 172.16.5.0 255.255.255.0 10.1.1.0 255.255.255.0
global (outside) 1 interface
nat (inside) 0 access-list ipsecvpn
nat (inside) 1 172.16.5.0 255.255.255.0
route outside 0.0.0.0 0.0.0.0 20.5.5.100 1
crypto ipsec transform-set hsfwa esp-3des esp-md5-hmac
crypto map vpnmap 10 match address ipsecvpn
crypto map vpnmap 10 set pfs
crypto map vpnmap 10 set peer 20.0.0.1
crypto map vpnmap 10 set transform-set hsfwa
crypto map vpnmap interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 20.0.0.1 type ipsec-l2l
tunnel-group 20.0.0.1 ipsec-attributes
pre-shared-key 123456
!
: end
ciscoasa# 测试验证:
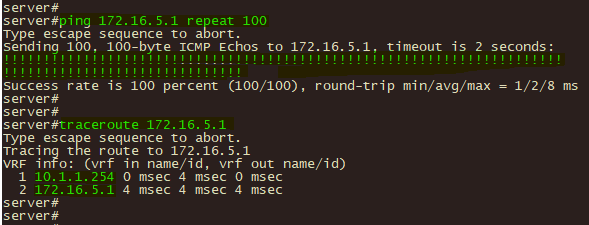
1、在总部或分支机构终端通过ping 和 tracert 测试至对端VPN资源的连通性和路径
2、总部山石防火墙通过 show isakmp sa 和show ipsec sa 查看验证ipsec 第一、第二阶段的协商状态
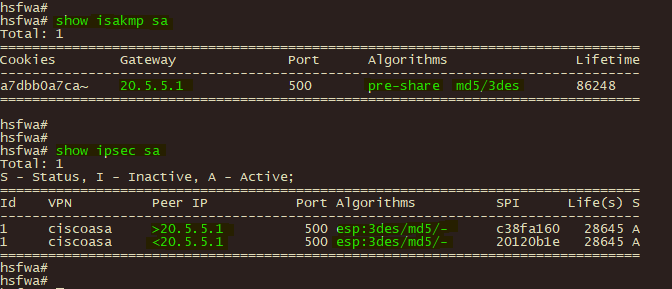
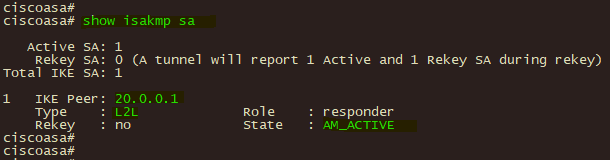
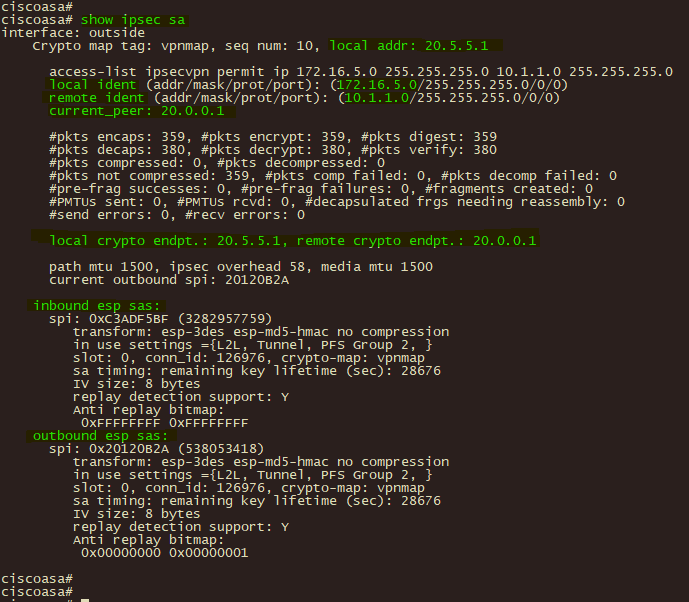
3、分支机构CISCO ASA 通过 show isakmp sa 和show ipsec sa 查看验证ipsec 第一、第二阶段的协商状态