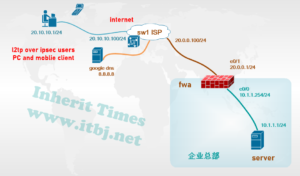
需求:企业总部部署山石防火墙为互联网出口网关;远程、移动办公人员需通过互联网访问企业内部服务器(10.1.1.0/24)
为提升信息系统安全级别,远程、移动办公用户需通过l2tp over ipsec 接入企业内网。
注意:l2tp over ipsec 在防火墙和PC win7、win10 终端安装配置相比ssl vpn稍复杂,推荐用户使用ssl vpn;
l2tp over ipsec 优点在于 PC winodws 系统、手机安卓系统内建客户端,无需安装额外软件。
防火墙关键配置:
fwa# show configuration
aaa-server “itbj.net” type local
user “l2tpuser1“
password “123456“
exit
user-group “inherit“
member user “l2tpuser1“
exit
exit
zone “untrust”
type wan
exit
zone “l2tpipsec“
vrouter “trust-vr”
exit
hostname “fwa”
isakmp proposal “l2tp_ipsec_p1“
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
exit
isakmp peer “l2tp_ipsec_client“
type usergroup
isakmp-proposal “l2tp_ipsec_p1“
pre-share “654321“
aaa-server “itbj.net“
nat-traversal
accept-all-peer-id
interface ethernet0/1
exit
ipsec proposal “l2tp_ipsec_p2“
hash md5 sha
encryption 3des des aes
lifetime 3600
lifesize 250000
exit
tunnel ipsec “l2tp_ipsec” auto
mode transport
isakmp-peer “l2tp_ipsec_client“
ipsec-proposal “l2tp_ipsec_p2“
accept-all-proxy-id
split-tunnel-route 10.1.1.0/24
exit
l2tp pool “l2tp_ipsec_pool“
address 10.1.99.1 10.1.99.100
dns 114.114.114.114
exit
tunnel l2tp “l2tp_ipsec“
pool “l2tp_ipsec_pool“
interface ethernet0/1
ppp-auth any
local-name “zbfwa”
next-tunnel ipsec “l2tp_ipsec“
aaa-server “itbj.net“
exit
interface ethernet0/0
zone “trust”
ip address 10.1.1.254 255.255.255.0
manage ssh
manage ping
manage snmp
exit
interface ethernet0/1
zone “untrust”
ip address 20.0.0.1 255.255.255.0
manage ping
exit
interface tunnel40
zone “l2tpipsec“
ip address 10.1.99.254 255.255.255.0
manage ping
tunnel l2tp “l2tp_ipsec“
reverse-route prefer
exit
ip vrouter “trust-vr”
snatrule id 1 from “10.1.1.0/24” to “Any” service “Any” eif ethernet0/1 trans-to eif-ip mode dynamicport
ip route 0.0.0.0/0 20.0.0.100
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 41
action permit
src-zone “l2tpipsec“
dst-zone “trust”
src-addr “Any”
dst-ip 10.1.1.0/24
service “Any”
user-group “itbj.net” “inherit“
exit
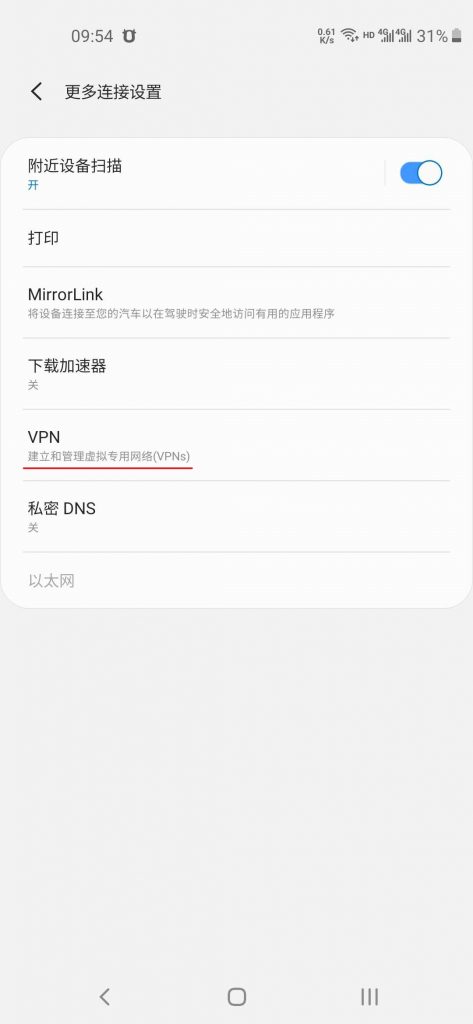
End一、安卓终端内建客户端配置
按图片顺序配置安卓手机VPN客户端
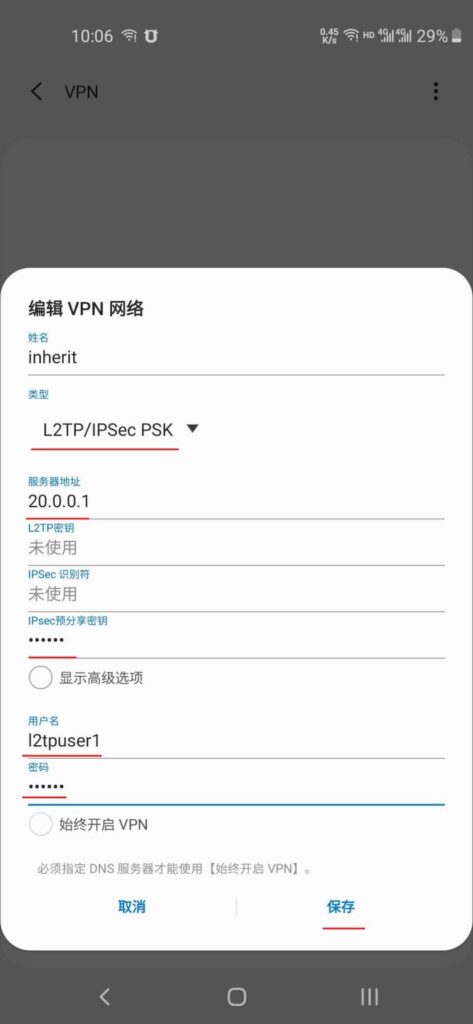
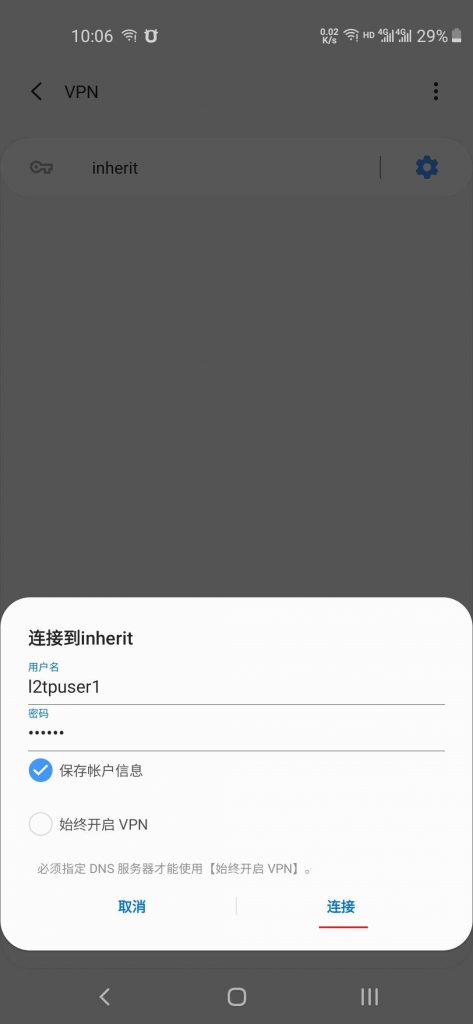

二、 windows 配置、测试
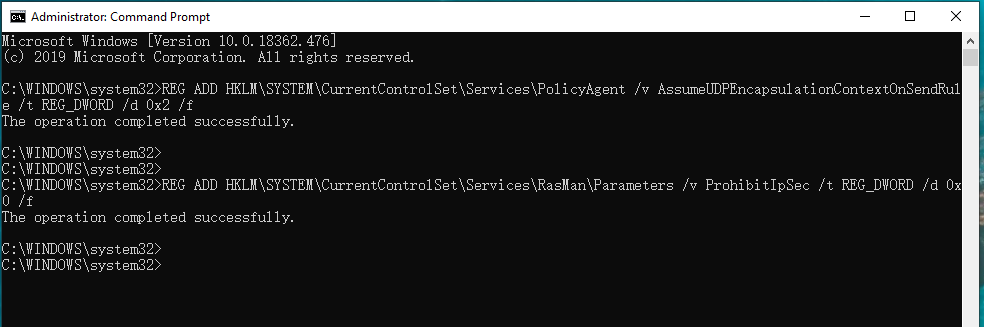
1、修改win10注册表,以管理员身份打开命令行窗口,复制以下注册信息在命令行窗口执行(注意复制执行第一行后再执行第二行,以免不成功报错),执行成功后,重新启动PC;
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\PolicyAgent /v AssumeUDPEncapsulationContextOnSendRule /t REG_DWORD /d 0x2 /f
REG ADD HKLM\SYSTEM\CurrentControlSet\Services\RasMan\Parameters /v ProhibitIpSec /t REG_DWORD /d 0x0 /f
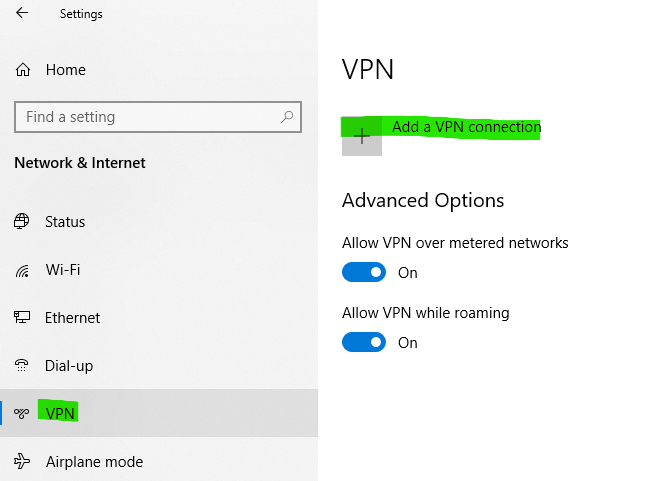
2、打开系统设置、添加VPN连接;
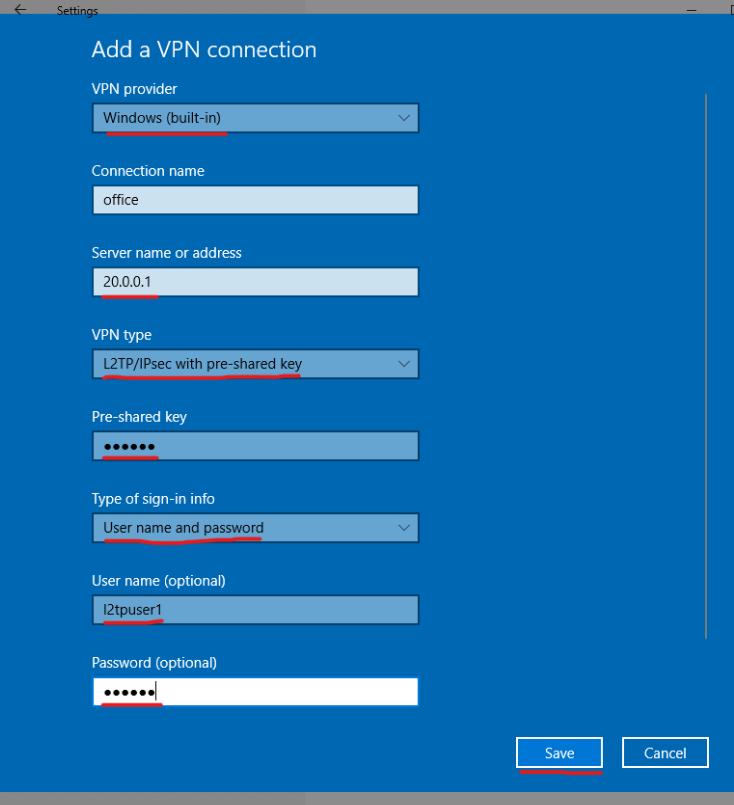
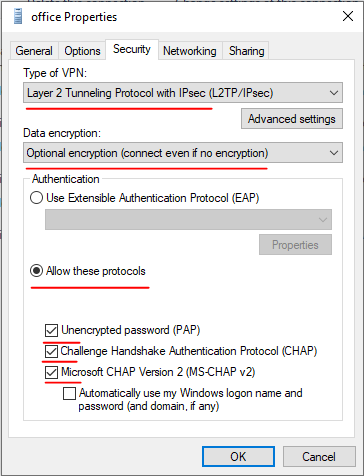
3、按下图选择windows内建客户端、VPN类型,并输入VPN网关地址及用户名、密码信息;
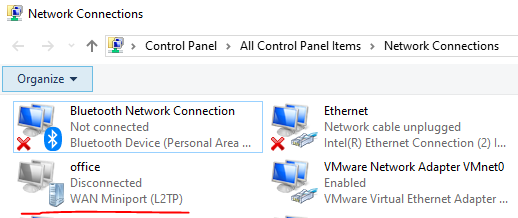
4、打开网卡连接选项,选择新建L2TP网卡,进入属性设置;
5、按图选择VPN类型,加密选项及协商协议;
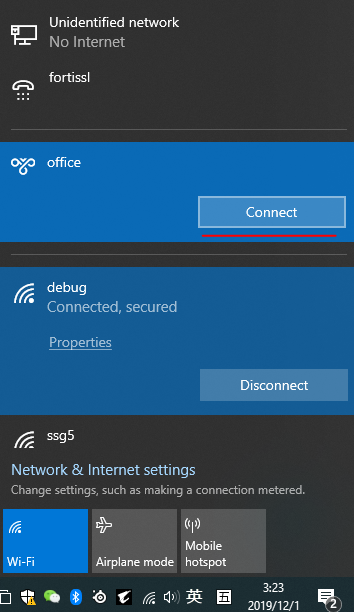
6、点击任务栏右下角网络图标,弹出网络状态菜单,选择新建立的网卡进行连接;
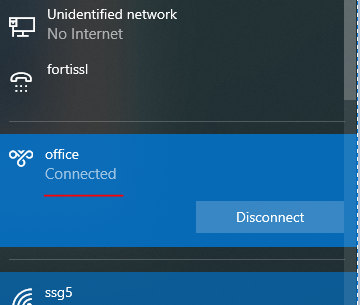
7、l2tp over ipsec 连接成功后网卡状态;
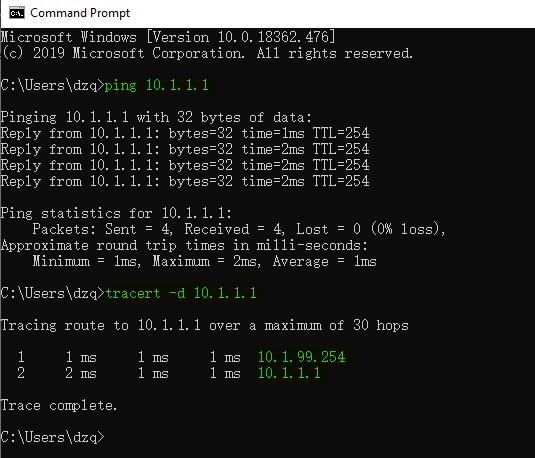
8、在终端PC上 通过ping 和tracert 验证测试至企业内部服务器连通性和路径。