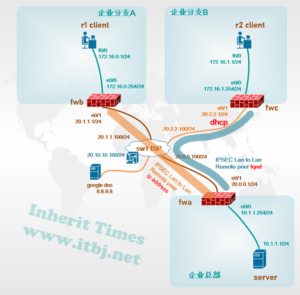
需求场景 企业总部与企业分支通过互联网建立VPN,总部与分支A使用固定IP地址,分支B为DHCP动态地址。
现状:
1、企业总部与企业分支A、B办公环境均已使用飞塔防火墙做为出口网关接入互联网;可访问互联网资源;
2、企业总部与企业分支A已建立IPSEC VPN
新增需求:
1、分支机构B与总部建立IPSEC VPN,实现机构间数据共享;
2、IPSEC VPN的配置不对用户访问互联网产生影响。
现网总部与分支A、B设备已配置源地址转换及安全策略,三个机构均可访问互联网,总部与分支A已建立IPSEC VPN。
防火墙关键配置如下:
fwa# show configuration
!
ip vrouter “trust-vr”
exit
zone “trust”
exit
zone “untrust”
exit
zone “ipsecvpn”
exit
interface tunnel10
exit
interface tunnel20
exit
zone “untrust”
type wan
exit
zone “ipsecvpn”
vrouter “trust-vr”
exit
hostname “fwa”
isakmp proposal “psk-md5-3des-g2“
hash md5
exit
isakmp peer “fzbfwc“
mode aggressive
type dynamic
isakmp-proposal “psk-md5-3des-g2”
pre-share 123456
local-id fqdn “zbfw“
peer-id fqdn “fzbfwc“
nat-traversal
accept-all-peer-id
interface ethernet0/1
exit
isakmp peer “fwb”
mode aggressive
isakmp-proposal “psk-md5-3des-g2”
pre-share 123456
peer 20.1.1.1
nat-traversal
interface ethernet0/1
exit
ipsec proposal “esp-md5-3des-g2“
hash md5
encryption 3des
group 2
exit
tunnel ipsec “fzb” auto
isakmp-peer “fzbfwc“
ipsec-proposal “esp-md5-3des-g2“
auto-connect
id local 10.1.1.0/24 remote 172.16.1.0/24 service “Any”
exit
tunnel ipsec “tofwb” auto
isakmp-peer “fwb”
ipsec-proposal “esp-md5-3des-g2”
auto-connect
id local 10.1.1.0/24 remote 172.16.0.0/24 service “Any”
exit
interface ethernet0/0
zone “trust”
ip address 10.1.1.254 255.255.255.0
manage ping
manage ssh
exit
interface ethernet0/1
zone “untrust”
ip address 20.0.0.1 255.255.255.0
manage ping
exit
interface tunnel20
zone “ipsecvpn”
manage ping
tunnel ipsec “fzb“
reverse-route prefer
exit
interface tunnel10
zone “ipsecvpn”
manage ping
tunnel ipsec “tofwb”
reverse-route prefer
exit
ip vrouter “trust-vr”
snatrule id 1 from “10.1.1.0/24” to “Any” service “Any” trans-to 20.0.0.1 mode dynamicport
ip route 0.0.0.0/0 20.0.0.100
ip route 172.16.1.0/24 tunnel20
ip route 172.16.0.0/24 tunnel10
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 11
action permit
src-zone “trust”
dst-zone “ipsecvpn”
src-ip 10.1.1.0/24
dst-ip 172.16.1.0/24
dst-ip 172.16.0.0/24
service “Any”
exit
rule id 12
action permit
src-zone “ipsecvpn”
dst-zone “trust”
src-addr “Any”
dst-ip 10.1.1.0/24
service “Any”
exit
Endfwc# show configuration
!
ip vrouter “trust-vr”
exit
zone “trust”
exit
zone “untrust”
exit
zone “ipsecvpn”
exit
interface tunnel20
exit
zone “untrust”
type wan
exit
zone “ipsecvpn”
vrouter “trust-vr”
exit
hostname “fwc”
isakmp proposal “psk-md5-3des-g2“
hash md5
exit
isakmp peer “fwa“
mode aggressive
isakmp-proposal “psk-md5-3des-g2”
pre-share “123456“
peer 20.0.0.1
local-id fqdn “fzbfwc“
peer-id fqdn “zbfw“
nat-traversal
interface ethernet0/1
exit
ipsec proposal “esp-md5-3des-g2“
hash md5
encryption 3des
group 2
exit
tunnel ipsec “tofwa” auto
isakmp-peer “fwa“
ipsec-proposal “esp-md5-3des-g2“
auto-connect
id local 172.16.1.0/24 remote 10.1.1.0/24 service “Any”
exit
interface ethernet0/0
zone “trust”
ip address 172.16.1.254 255.255.255.0
manage ping
manage ssh
exit
interface ethernet0/1
zone “untrust”
ip address 20.1.1.1 255.255.255.0
manage ping
exit
interface tunnel20
zone “ipsecvpn“
manage ping
tunnel ipsec “tofwa“
reverse-route prefer
exit
ip vrouter “trust-vr”
snatrule id 1 from “172.16.0.0/24” to “Any” service “Any” trans-to 20.1.1.1 mode dynamicport
ip route 0.0.0.0/0 20.1.1.100
ip route 10.1.1.0/24 tunnel20
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 11
action permit
src-zone “trust”
dst-zone “ipsecvpn”
src-ip 172.16.1.0/24
dst-ip 10.1.1.0/24
service “Any”
exit
rule id 12
action permit
src-zone “ipsecvpn”
dst-zone “trust”
src-ip 20.0.0.0/24
dst-ip 172.16.1.0/24
service “Any”
exit
End验证:
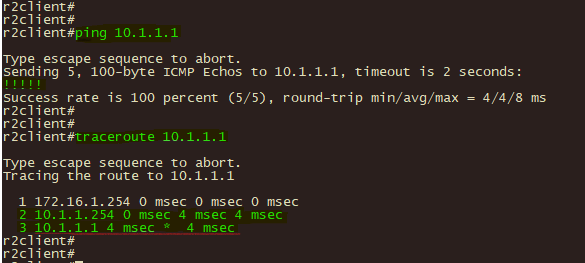
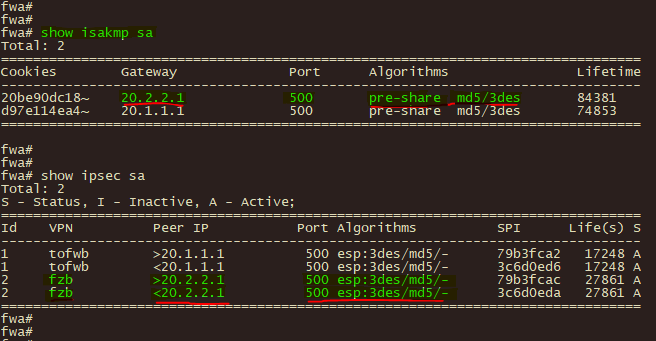
1、在防火墙fwa、fwc上使用show isakmp sa和 show ipsec sa 命令查企IPSEC IKE第一阶段、第二阶段协商状态

2、在分支机构B使用ping和tracert 命令测试至总部服务器10.1.1.1的可达性和路径