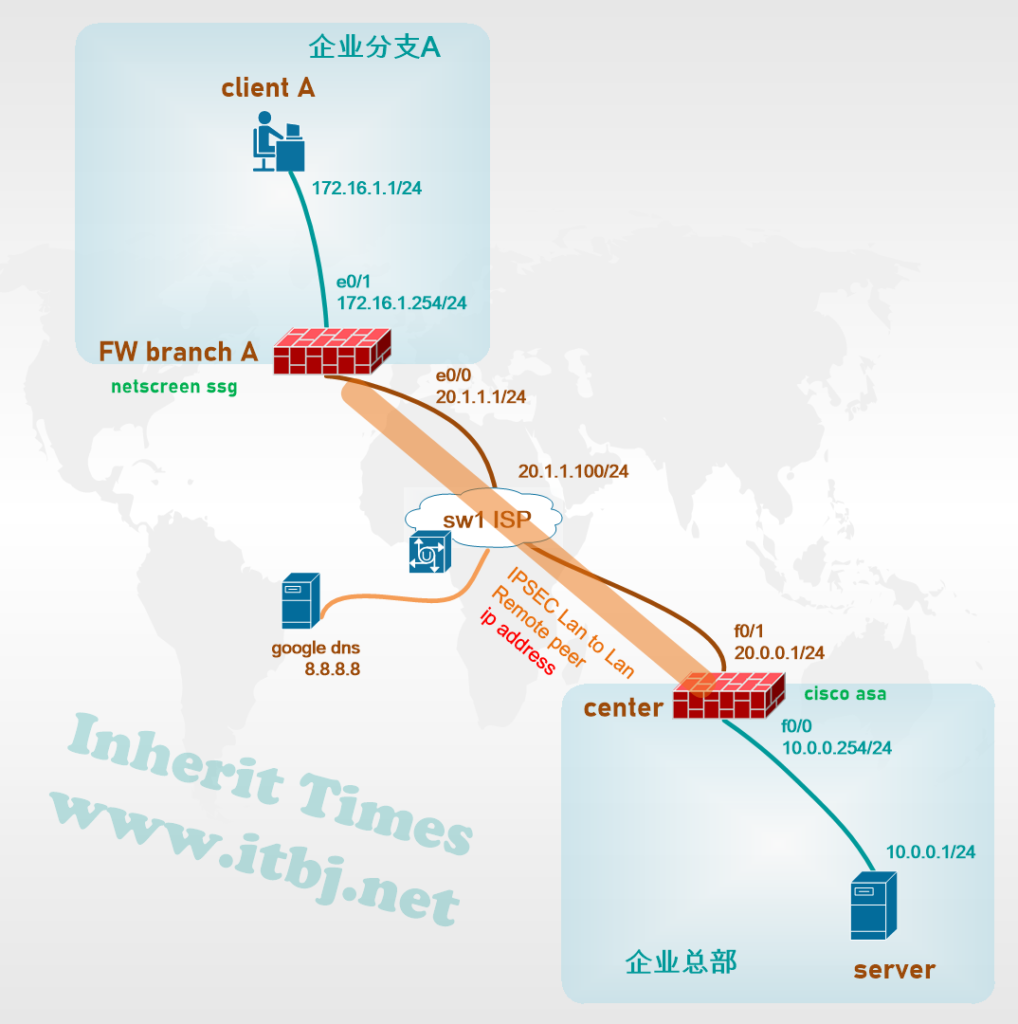
需求:企业分支机构A部署netscreen ssg防火墙 为互联网出口网关,并与总部cisco asa 建立ipsec vpn。
总部CISCO ASA配置:
center# show running-config
ASA Version 8.4(7)31
!
hostname center
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
switchport access vlan 20
!
interface Vlan10
nameif inside
security-level 100
ip address 10.0.0.254 255.255.255.0
!
interface Vlan20
nameif outside
security-level 0
ip address 20.0.0.1 255.255.255.0
!
object network obj-10.0.0.0
subnet 10.0.0.0 255.255.255.0
object network obj-172.16.1.0
subnet 172.16.1.0 255.255.255.0
access-list untrust extended permit icmp any any
access-list ipsecvpn extended permit ip 10.0.0.0 255.255.255.0 172.16.1.0 255.255.255.0
nat (inside,outside) source static obj-10.0.0.0 obj-10.0.0.0 destination static obj-172.16.1.0 obj-172.16.1.0
!
object network obj-10.0.0.0
nat (inside,outside) dynamic interface
access-group untrust in interface outside
route outside 0.0.0.0 0.0.0.0 20.0.0.100 1
crypto ipsec ikev1 transform-set ikev1tran esp-3des esp-md5-hmac
crypto map vpnmap 10 match address ipsecvpn
crypto map vpnmap 10 set pfs
crypto map vpnmap 10 set peer 20.1.1.1
crypto map vpnmap 10 set ikev1 phase1-mode aggressive
crypto map vpnmap 10 set ikev1 transform-set ikev1tran
crypto map vpnmap 10 set security-association lifetime seconds 3600
crypto map vpnmap interface outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 20.1.1.1 type ipsec-l2l
tunnel-group 20.1.1.1 ipsec-attributes
ikev1 pre-shared-key 123456
!
: end分支A netscreen ssg防火墙配置:
fw-branch-A-> get config
set interface “ethernet0/0” zone “Untrust“
set interface “bgroup0” zone “Trust“
set interface bgroup0 port ethernet0/1
set interface ethernet0/0 ip 20.1.1.1/24
set interface ethernet0/0 route
set interface bgroup0 ip 172.16.1.254/24
set interface bgroup0 route
set interface bgroup0 ip manageable
set interface ethernet0/0 manage ping
set interface ethernet0/0 manage ssh
set hostname fw-branch-A
set address “Trust” “ipseclocal” 172.16.1.0 255.255.255.0
set address “Untrust” “ipsecremote” 10.0.0.0 255.255.255.0
set ike p1-proposal “ikepro” preshare group2 esp 3des md5 second 86400
set ike p2-proposal “ipsecpro” group2 esp 3des md5 second 3600
set ike gateway “center” address 20.0.0.1 Aggr outgoing-interface “ethernet0/0” preshare 123456 proposal “ikepro“
set vpn “centeripsec” gateway “center” no-replay tunnel idletime 0 proposal “ipsecpro“
set vpn “centeripsec” proxy-id local-ip 172.16.1.0/24 remote-ip 10.0.0.0/24 “ANY”
set policy id 2 name “ipsecvpn” from “Trust” to “Untrust” “ipseclocal” “ipsecremote” “ANY” tunnel vpn “centeripsec” id 0x1 pair-policy 3
set policy id 2
exit
set policy id 1 from “Trust” to “Untrust” “Any” “Any” “ANY” nat src permit
set policy id 1
exit
set policy id 3 name “ipsecvpn” from “Untrust” to “Trust” “ipsecremote” “ipseclocal” “ANY” tunnel vpn “centeripsec” id 0x1 pair-policy 2
set policy id 3
exit
set route 0.0.0.0/0 gateway 20.1.1.100
exit
fw-branch-A->
……
注意调整策略顺序,IPSEC VPN策略置与NAT策略之前!验证测试:
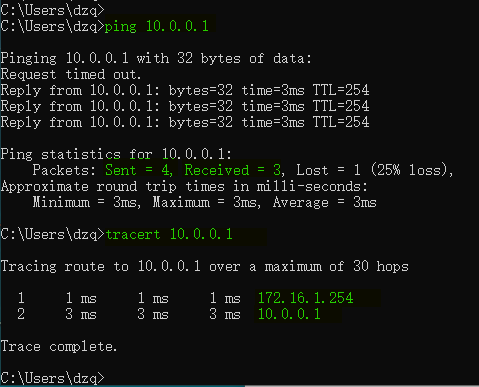
1、分支终端 ping 和 tracert 总部服务器,验证联通性和路径;
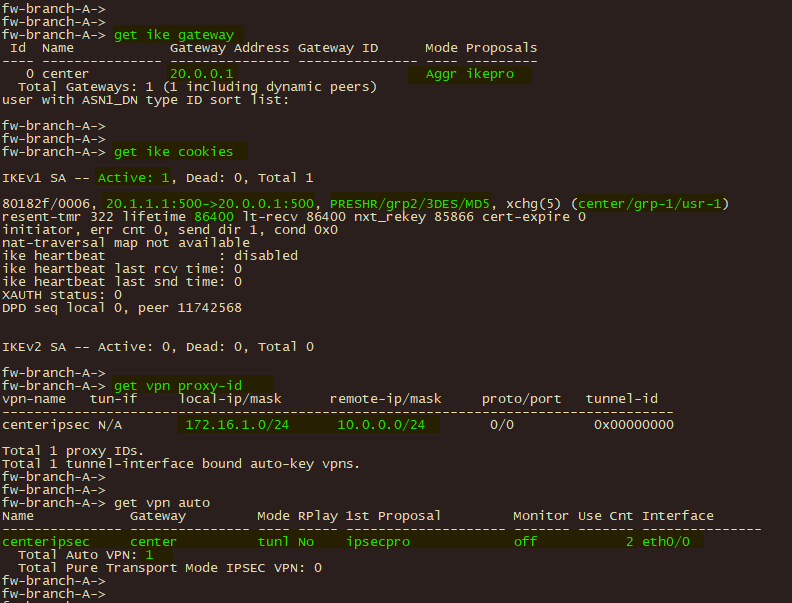
2、分支netscreen防火墙 get ik gateway , get ike cookies , get vpn proxy-id 验证IPSEC 对等体状态及 ike协商状态;
3、总部服务器 ping 和 traceroute 分支终端或网关,验证联通性及路径;
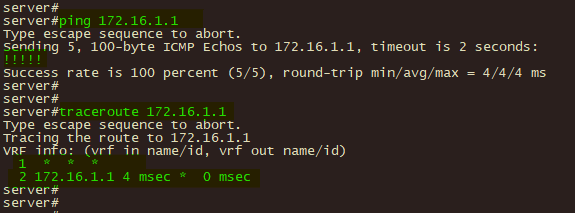
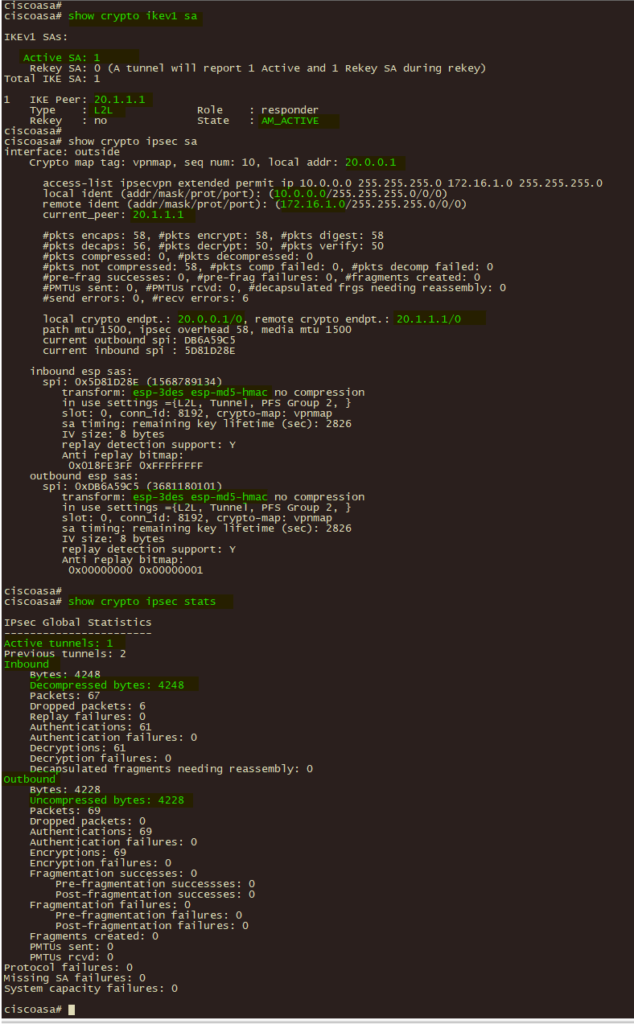
4、总部ASA 使用 show crypto ikev1 sa 及 show crypto ipsec sa 和 show crypto ipsec stats 验证ipsec vpn 第一、二阶段协商状态及数据加解密状态。