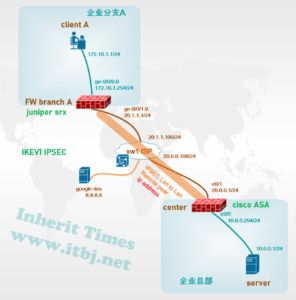
需求:企业分支机构A部署Juniper SRX防火墙 为互联网出口网关,并与总部cisco asa 建立ipsec vpn;
IKEV1
Juniper SRX IPSEC 基于路由。
企业总部CISCO ASA配置:
center# show run
:
ASA Version 9.1(7)32
!
hostname center
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
switchport access vlan 20
!
interface Vlan10
nameif inside
security-level 100
ip address 10.0.0.254 255.255.255.0
!
interface Vlan20
nameif outside
security-level 0
ip address 20.0.0.1 255.255.255.0
!
object network localvpn
subnet 10.0.0.0 255.255.255.0
object network remotevpn
subnet 172.16.1.0 255.255.255.0
access-list ipsecvpn extended permit ip object localvpn object remotevpn
access-list untrust extended permit icmp any4 any4
access-list trust extended permit icmp any any
nat (inside,outside) source static localvpn localvpn destination static remotevpn remotevpn
!
object network localvpn
nat (inside,outside) dynamic interface
access-group trust in interface inside
access-group untrust in interface outside
route outside 0.0.0.0 0.0.0.0 20.0.0.100 1
crypto ipsec ikev1 transform-set ipsectran esp-3des esp-md5-hmac
crypto ipsec security-association lifetime seconds 86400
crypto map vpnmap 10 match address ipsecvpn
crypto map vpnmap 10 set pfs
crypto map vpnmap 10 set peer 20.1.1.1
crypto map vpnmap 10 set ikev1 phase1-mode aggressive
crypto map vpnmap 10 set ikev1 transform-set ipsectran
crypto map vpnmap 10 set security-association lifetime seconds 86400
crypto map vpnmap interface outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
management-access inside
tunnel-group 20.1.1.1 type ipsec-l2l
tunnel-group 20.1.1.1 ipsec-attributes
ikev1 pre-shared-key 123456
!
: end企业分支A Juniper SRX配置:
root@branchA# show
version 12.1X46-D81;
system {
host-name branchA;
}
services {
ssh;
telnet;
xnm-clear-text;
web-management {
http {
interface ge-0/0/0.0;
}
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 172.16.1.254/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 20.1.1.1/24;
}
}
}
st0 {
unit 0 {
family inet;
family inet6;
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 20.1.1.100;
route 10.0.0.0/24 next-hop st0.0;
}
}
security {
key-protection;
ike {
respond-bad-spi 1;
proposal ikepro {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm md5;
encryption-algorithm 3des-cbc;
lifetime-seconds 86400;
}
policy ikepolicy {
mode aggressive;
proposals ikepro;
pre-shared-key ascii-text 123456
}
gateway ikegate {
ike-policy ikepolicy;
address 20.0.0.1;
dead-peer-detection {
always-send;
interval 10;
threshold 5;
}
local-identity inet 20.1.1.1;
remote-identity inet 20.0.0.1;
external-interface ge-0/0/1.0;
version v1-only;
}
}
ipsec {
vpn-monitor-options {
interval 10;
threshold 10;
}
proposal ipsecpro {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 86400;
}
policy ipsecpolicy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsecpro;
}
vpn ipsecvpn {
bind-interface st0.0;
vpn-monitor {
optimized;
destination-ip 20.0.0.1;
}
ike {
gateway ikegate;
proxy-identity {
local 172.16.1.0/24;
remote 10.0.0.0/24;
service any;
}
ipsec-policy ipsecpolicy;
}
establish-tunnels immediately;
}
}
nat {
source {
rule-set snat {
from zone trust;
to zone untrust;
rule pat {
match {
source-address 172.16.1.0/24;
}
then {
source-nat {
interface;
}
}
}
}
}
}
policies {
from-zone trust to-zone untrust {
policy snat {
match {
source-address localvpn;
destination-address any;
application any;
}
then {
permit;
}
}
}
default-policy {
permit-all;
}
policy-rematch;
}
zones {
security-zone trust {
address-book {
address localvpn 172.16.1.0/24;
}
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone untrust {
address-book {
address remotevpn 10.0.0.0/24;
}
screen untrust-screen;
host-inbound-traffic {
system-services {
ping;
traceroute;
ike;
}
}
interfaces {
ge-0/0/1.0;
st0.0;
}
}
}
}
[edit]
root@branchA#测试验证:
1、分支企业A终端ping 和 tracert 总部服务器 10.0.0.1 , 验证IPSEC VPN 连通性及路径;
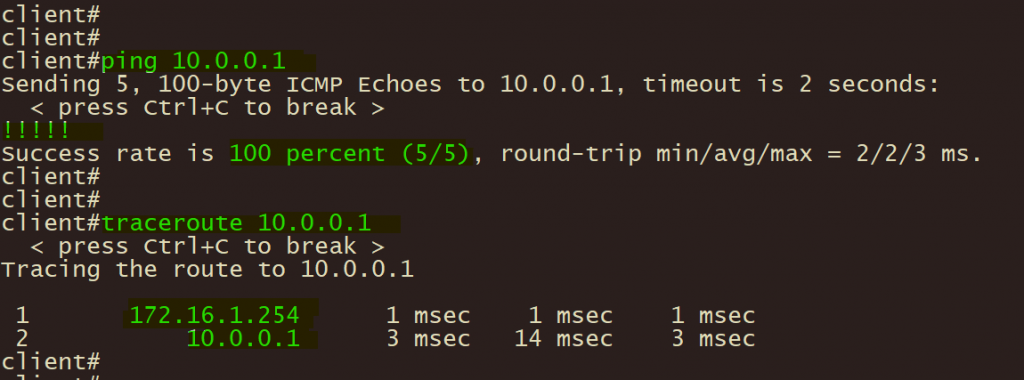
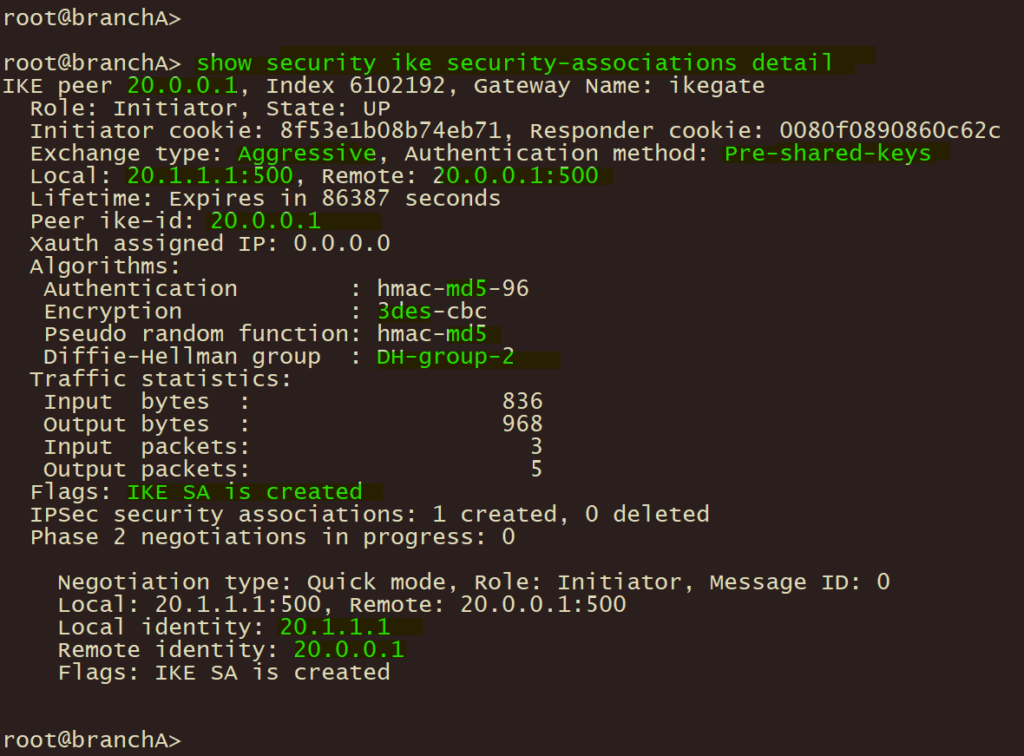
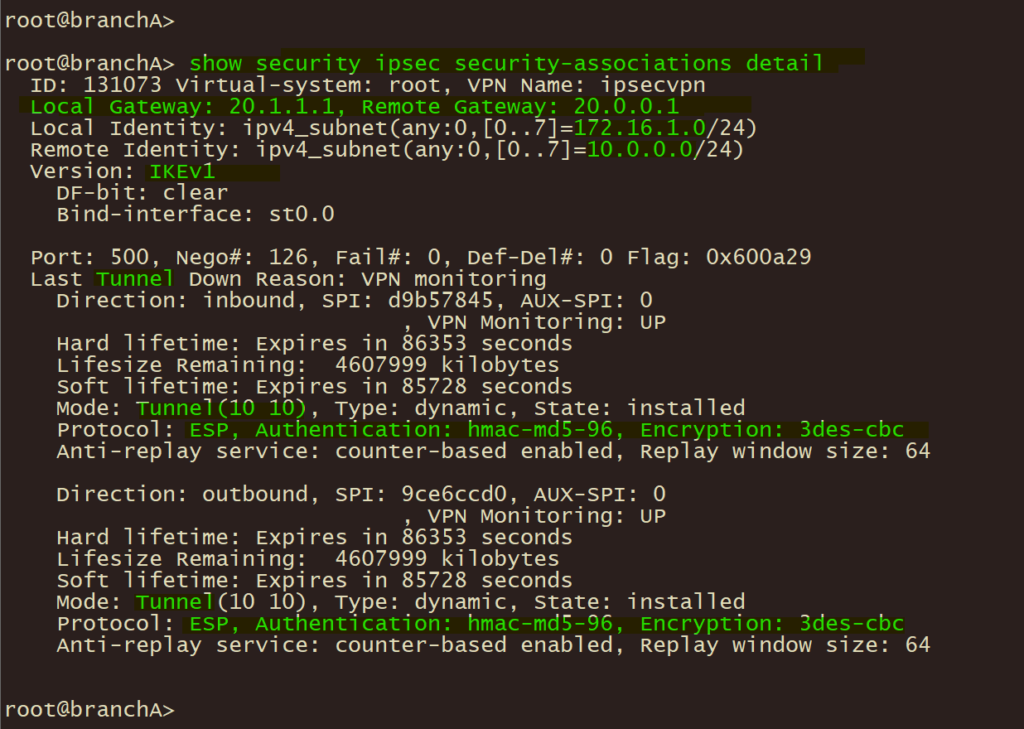
2、分支企业A 使用以下命令验证 IPSEC 第一/二阶段协调状态;
show security ike security-associations detail
show security ipsec security-associations detail
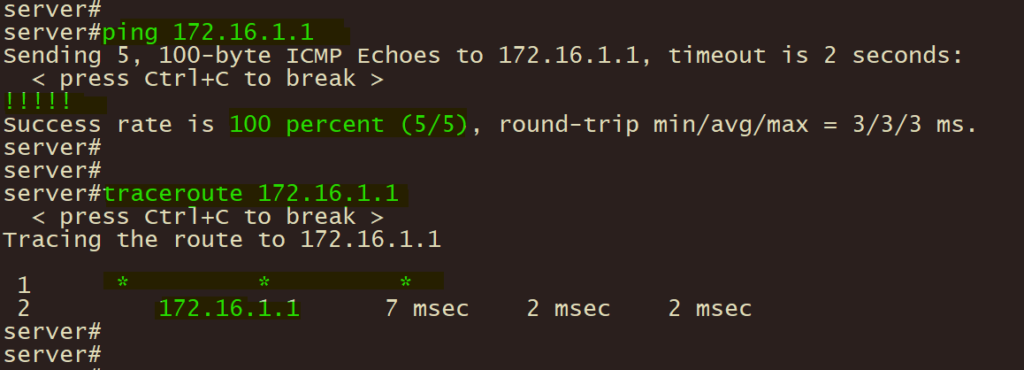
3、总服服务器 ping 和 tracert 分支企业终端验证 IPSEC VPN连通性和路径;
4、企业总部CISCO ASA 使用以下命令验证IPSEC 第一\二阶段协调状态及IPSEC 加密状态;
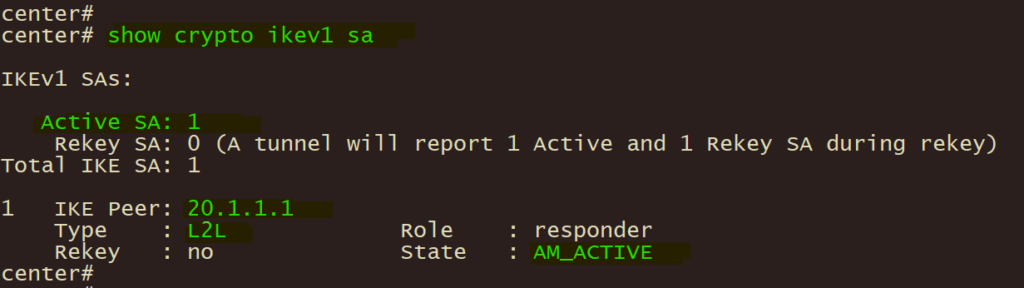
show crypto ikev1 sa
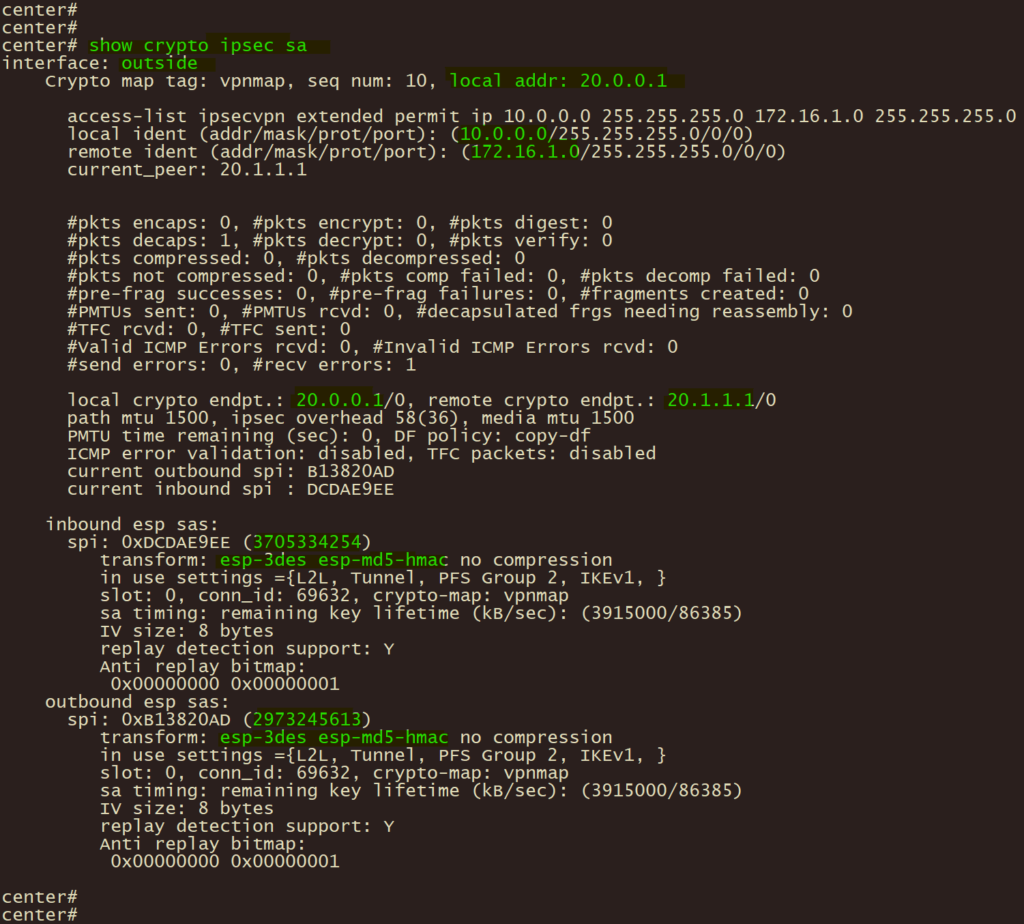
show crypto ipsec sa
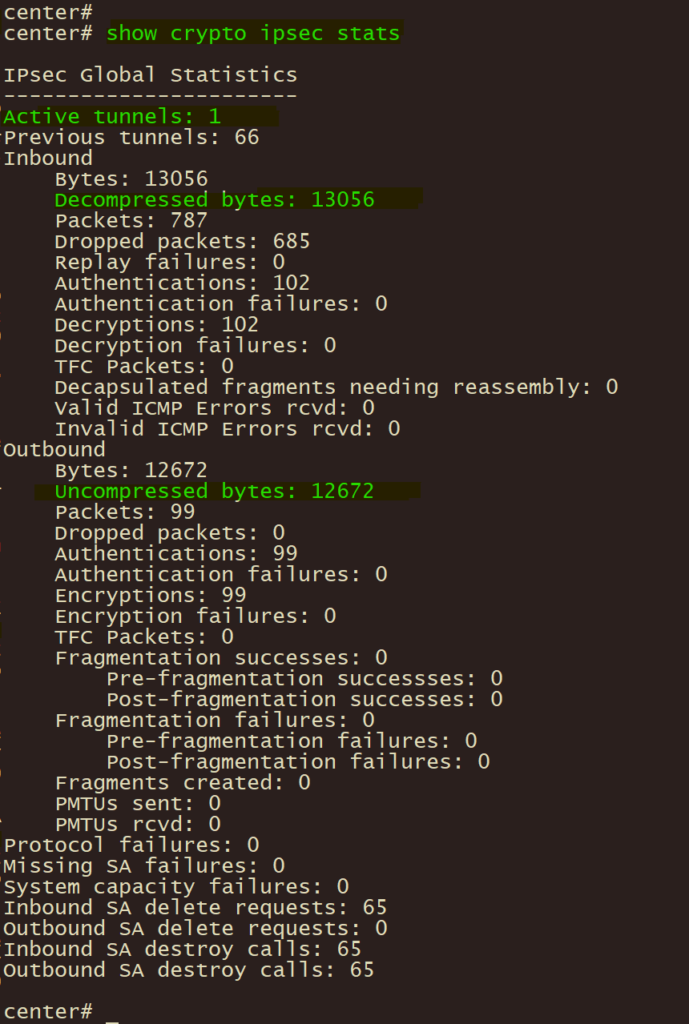
show crypto ipsec stats