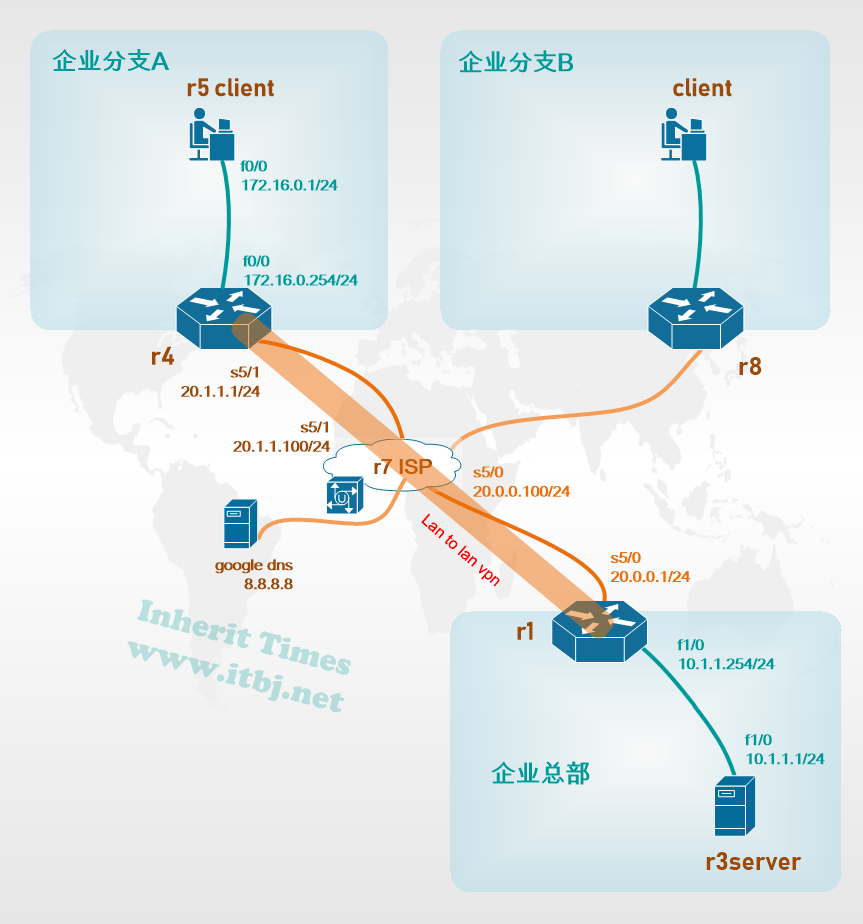
预配置
企业总部内网和企业分支A内网分别使用私有IP地址段 10.0.0.0/8和172.16.0.0/16,均已在网关路由器上配置源NAT (PAT)以访问互联网 google dns 8.8.8.8。
r1
!
hostname r1
!
interface FastEthernet1/0
ip address 10.1.1.254 255.255.255.0
ip nat inside
no shutdown
!
interface Serial5/0
ip address 20.0.0.1 255.255.255.0
ip nat outside
no shutdown
!
ip route 0.0.0.0 0.0.0.0 20.0.0.100
!
ip nat inside source list internet interface Serial5/0 overload
!
ip access-list standard internet
permit 10.1.1.0 0.0.0.255
!
end
r3server
!
hostname r3server
!
interface FastEthernet1/0
ip address 10.1.1.1 255.255.255.0
no shutdown
!
no ip routing
!
ip default-gateway 10.1.1.254
!
endr7isp#
!
hostname r7isp
!
interface Loopback0
ip address 8.8.8.8 255.255.255.255
!
interface Serial5/0
ip address 20.0.0.100 255.255.255.0
serial restart-delay 0
!
interface Serial5/1
ip address 20.1.1.100 255.255.255.0
no shutdown
!
end
r4#
!
hostname r4
!
interface FastEthernet0/0
ip address 172.16.0.254 255.255.255.0
ip nat inside
no shutdwon
!
interface Serial5/1
ip address 20.1.1.1 255.255.255.0
ip nat outside
no shutdown
!
ip route 0.0.0.0 0.0.0.0 20.1.1.100
!
ip nat inside source list to_int interface Serial5/1 overload
!
ip access-list standard to_int
permit any
!
end
r5client#
!
hostname r5client
!
interface FastEthernet0/0
ip address 172.16.0.1 255.255.255.0
no shutdown
!
no ip routing
!
ip default-gateway 172.16.0.254
!
end需求场景 两机构间建立LAN TO LAN (site to site) ipsec vpn
企业总部与企业分支A均已接入互联网,为保障信息安全,现两机构间需建立VPN,使分支机构内网访问总部服务器r3server资源的流量进行IPSEC 加密。
配置如下:
第一步: 变更r1、r4的NAT配置
(IPSEC LAN TO LAN VPN 需明确定义匹配加密流量 源地址-目的地址,原NAT配置为企业总部和企业分支A 内部用户访问互联网均转换为其接口地址,更改NAT配置使IPSEC VPN加密流量不进行NAT地址转换(NAT排除/豁免)。
更改原NAT配置
———————————————————————————-
r1#
!
no ip nat inside source list internet interface Serial5/0 overload
!
no ip access-list standard internet
!
ip access-list extended internet
deny ip 10.1.1.0 0.0.0.255 172.16.0.0 0.0.0.255
permit ip any any
!
ip nat inside source list internet interface Serial5/0 overload
!
end
———————————————————————————-
r4#
!
no ip nat inside source list to_int interface Serial5/1 overload
!
no ip access-list standard to_int
!
ip access-list extended to_int
deny ip 172.16.0.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip any any
!
ip nat inside source list to_int interface Serial5/1 overload
!
end
———————————————————————————-
第二步: r1、r4 配置IPSEC VPN
———————————————————————————-
r1#
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key test address 20.1.1.1
!
crypto ipsec transform-set testipsec esp-3des esp-md5-hmac
!
ip access-list extended testvpn
permit ip 10.1.1.0 0.0.0.255 172.16.0.0 0.0.0.255
!
crypto map testmap 10 ipsec-isakmp
set peer 20.1.1.1
set transform-set testipsec
match address testvpn
!
interface Serial5/0
crypto map testmap
!
end
———————————————————————————-
r4#
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key test address 20.0.0.1
!
crypto ipsec transform-set testipsec esp-3des esp-md5-hmac
!
ip access-list extended testvpn
permit ip 172.16.0.0 0.0.0.255 10.1.1.0 0.0.0.255
!
crypto map testmap 10 ipsec-isakmp
set peer 20.0.0.1
set transform-set testipsec
match address testvpn
!
interface Serial5/1
crypto map testmap
!
end验证:
在r5client (172.16.0.0.1) 上 ping r3server (10.1.1.1)
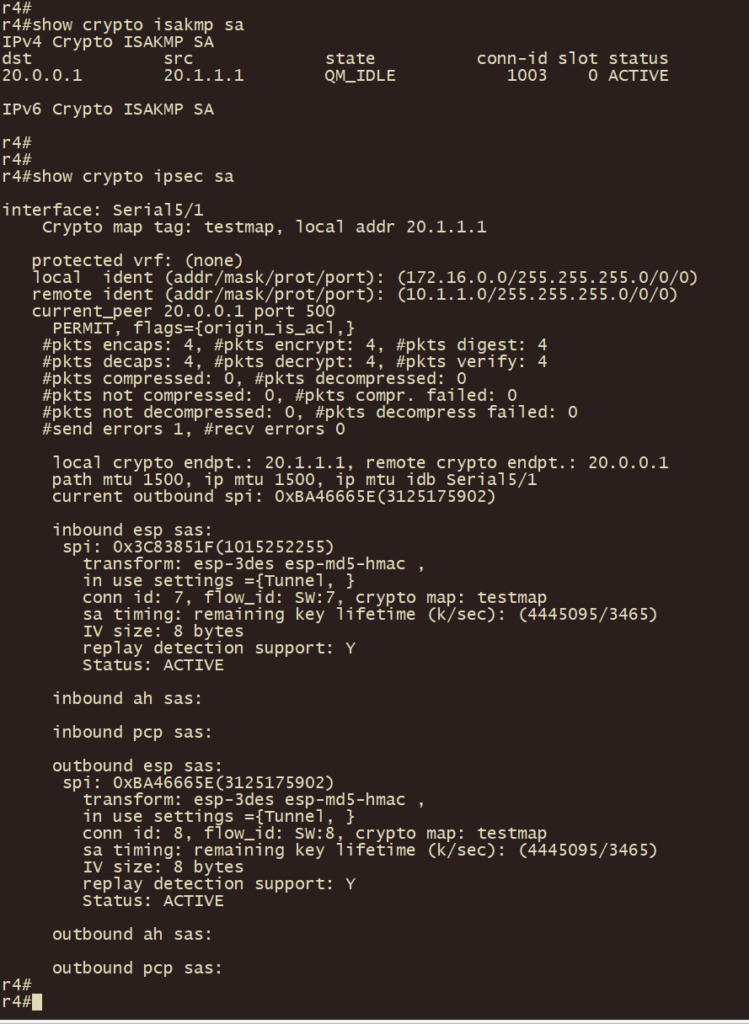
r4、r1上使用show crypto isakmp sa 和 show crypto ipsec sa 以及show crypto engine connections active 命令查看 IPSEC VPN建立状态及加密状态
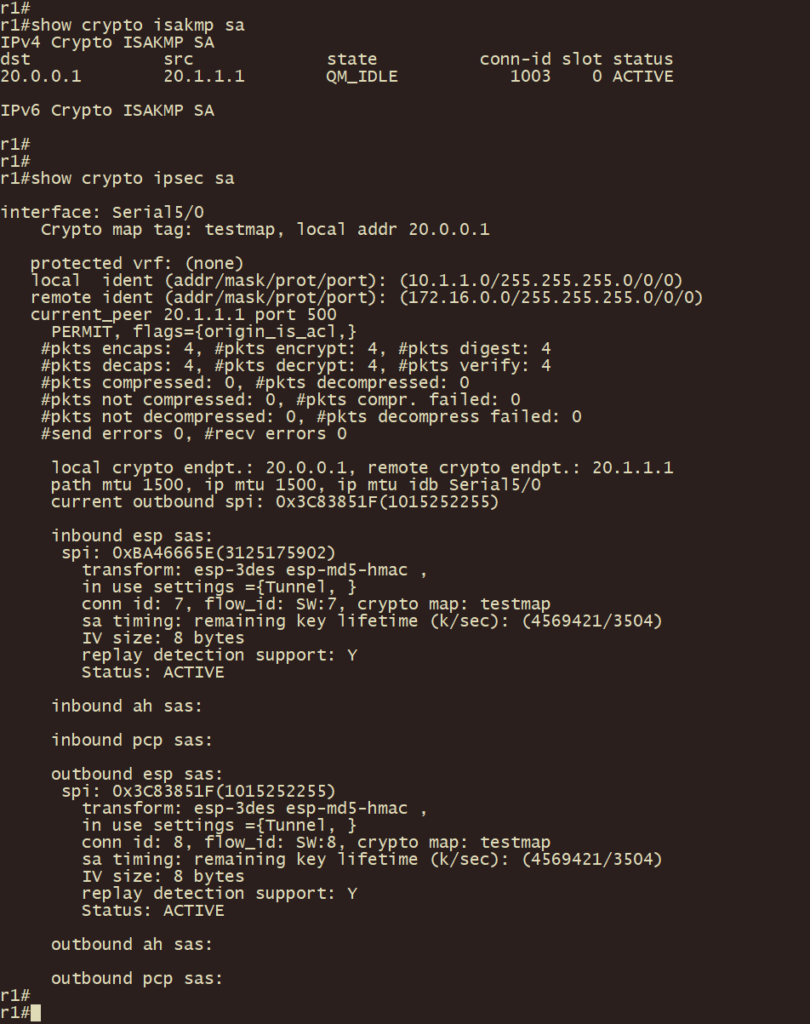
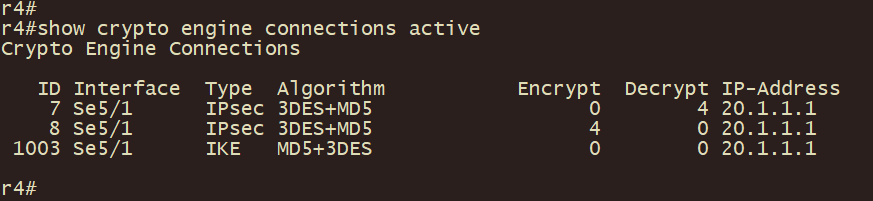
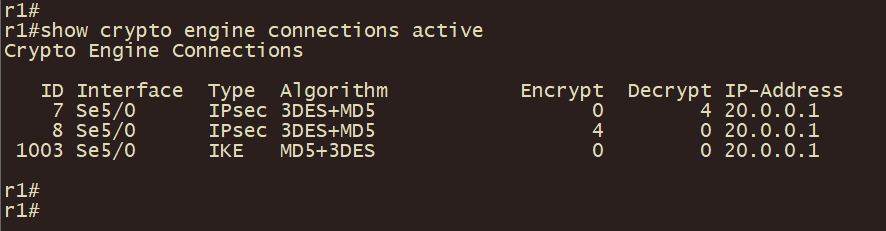
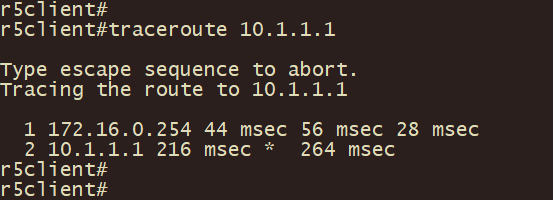
r5client上traceroute 10.1.1.1
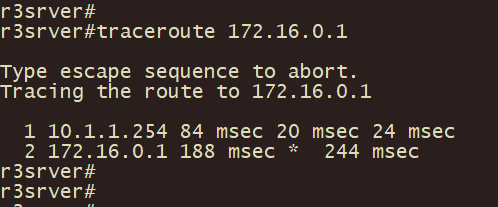
r3server上traceroute 172.16.0.1, 查看IPSEV VPN建立后,加密流量路径