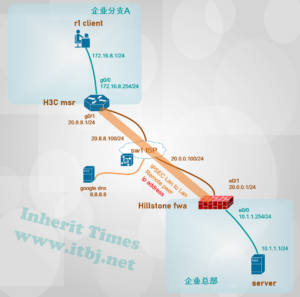
需求:企业新分支机构A部署H3C msr路由器 做为互联网出口网关,与总部山石防火墙建立IPSEC VPN 以实现资源共享
山石防火墙配置:
hsfwa# show configuration
!
Version 5.5R4
zone “untrust”
type wan
exit
zone “ipsecvpn“
vrouter “trust-vr”
exit
hostname “hsfwa“
isakmp proposal “psk-md5-3des-g2“
hash md5
exit
isakmp peer “h3cmsr“
mode aggressive
isakmp-proposal “psk-md5-3des-g2”
pre-share “123456“
peer 20.8.8.1
nat-traversal
accept-all-peer-id
interface ethernet0/1
exit
ipsec proposal “esp-md5-3des-g2“
hash md5
encryption 3des
group 2
exit
tunnel ipsec “tomsr” auto
isakmp-peer “h3cmsr“
ipsec-proposal “esp-md5-3des-g2“
auto-connect
description “to_h3c_msr”
id local 10.1.1.0/24 remote 172.16.8.0/24 service “any”
exit
interface ethernet0/0
zone “trust”
ip address 10.1.1.254 255.255.255.0
manage ssh
manage ping
exit
interface ethernet0/1
zone “untrust”
ip address 20.0.0.1 255.255.255.0
manage ping
exit
interface tunnel80
zone “ipsecvpn“
manage ping
tunnel ipsec “tomsr“
exit
ip vrouter “trust-vr”
snatrule id 1 from “10.1.1.0/24” to “Any” service “Any” trans-to eif-ip mode dynamicport
ip route 0.0.0.0/0 20.0.0.100
ip route 172.16.8.0/24 tunnel80
exit
rule id 1
action permit
src-zone “trust”
dst-zone “untrust”
src-addr “Any”
dst-addr “Any”
service “Any”
exit
rule id 81
action permit
src-zone “trust”
dst-zone “ipsecvpn“
src-ip 10.1.1.0/24
dst-ip 172.16.8.0/24
service “Any”
exit
rule id 82
action permit
src-zone “ipsecvpn“
dst-zone “trust”
src-ip 172.16.8.0/24
dst-ip 10.1.1.0/24
service “Any”
exit
Endh3c msr 路由器配置:
[h3cmsr]display current-configuration
#
version 7.1.064, Release 0707P16
#
sysname h3cmsr
#
interface GigabitEthernet0/0
port link-mode route
ip address 172.16.8.254 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
ip address 20.8.8.1 255.255.255.0
nat outbound name snat
ipsec apply policy hspolicy
#
ip route-static 0.0.0.0 0 GigabitEthernet0/1 20.8.8.100
#
acl advanced name snat
rule 1 deny ip source 172.16.8.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 10 permit ip source 172.16.8.0 0.0.0.255
#
acl advanced name vpnacl
rule 10 permit ip source 172.16.8.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
ipsec transform-set hspeer
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2
#
ipsec policy-template pt 10
transform-set hspeer
security acl name vpnacl
local-address 20.8.8.1
remote-address 20.0.0.1
ike-profile hsikepro
#
ipsec policy hspolicy 10 isakmp template pt
#
ike profile hsikepro
keychain hskey
exchange-mode aggressive
match remote identity address 20.0.0.1 255.255.255.255
proposal 10
#
ike proposal 10
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain hskey
pre-shared-key address 20.0.0.1 255.255.255.255 key simple 123456
#
return测试验证:
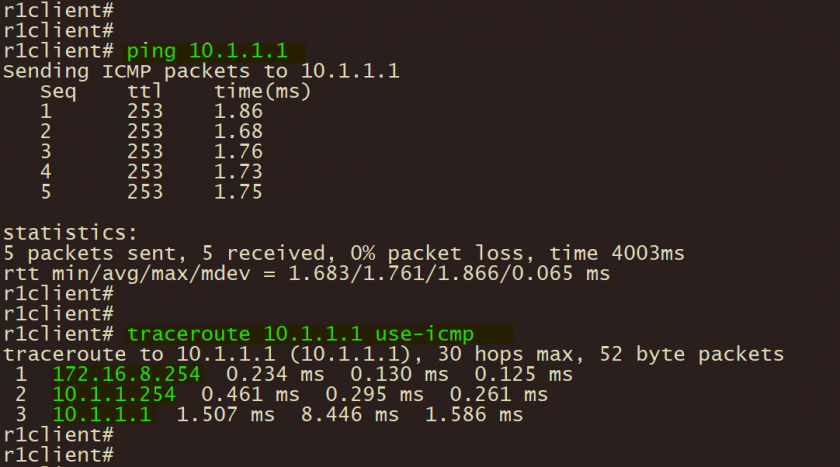
1、分支机构终端通过ping 和 tracerouter 测试至总部服务器连通性;
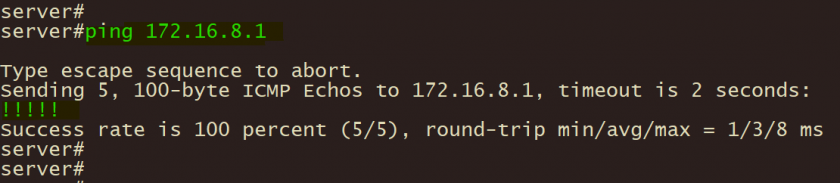
2、总部服务器通过ping 测试至分支A终端联通性;
3、总部山石防火墙通过 show isakmp sa 和 show ipsec sa 验证 ike ipsec 协商状态;
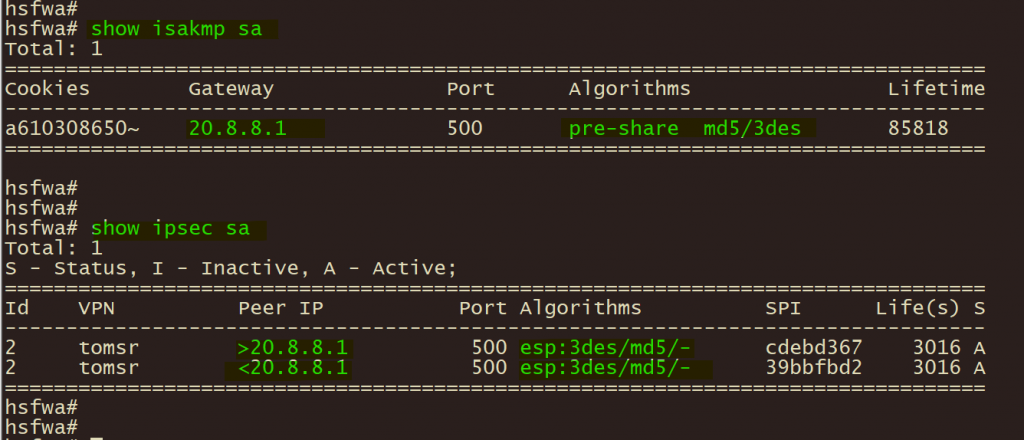
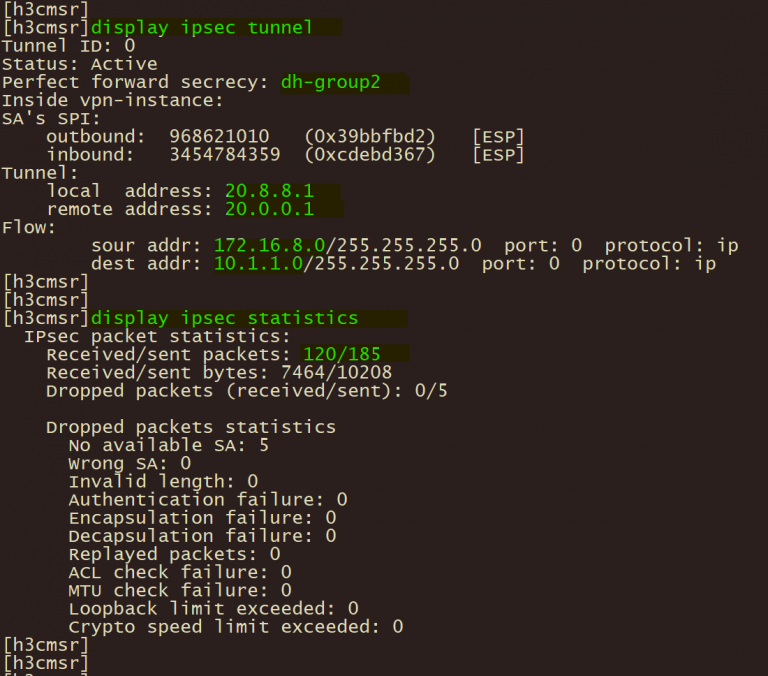
4、分支A华三路由器使用 display ike 和 display ipsec sa验证ike ipsec 协商状态;
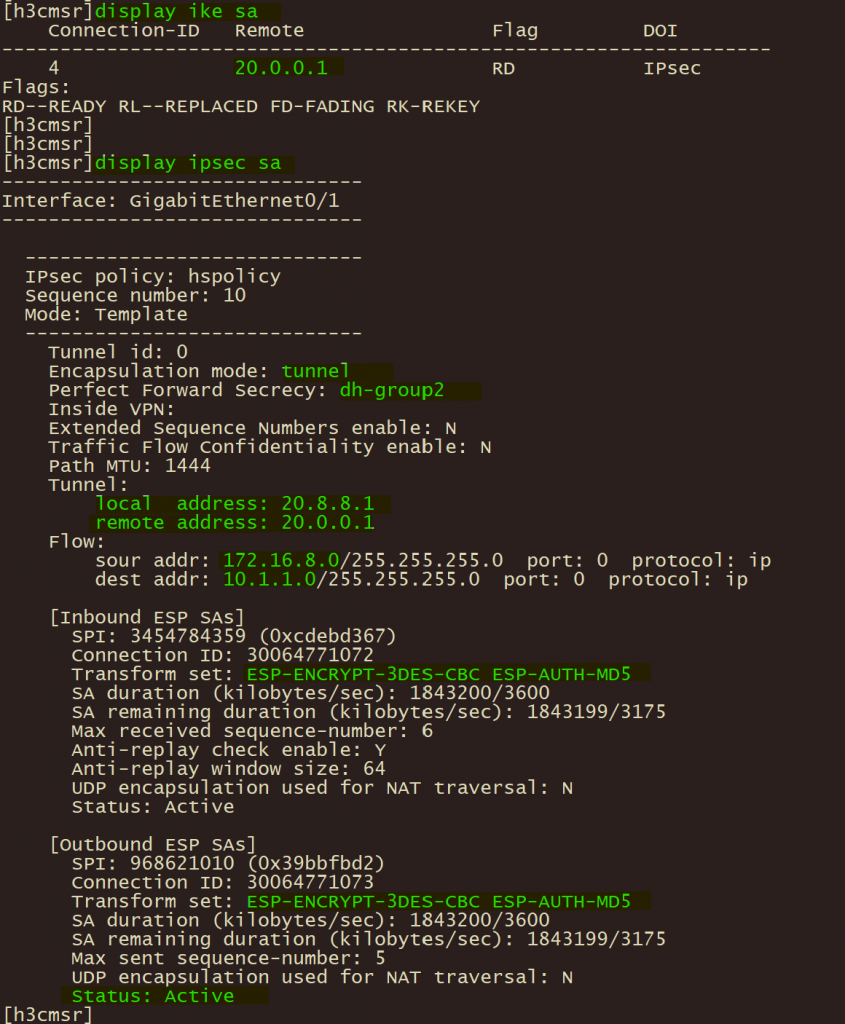
5、分支华三路由器使用 display ipsec tunnel 验证 ipsec 隧道状态。