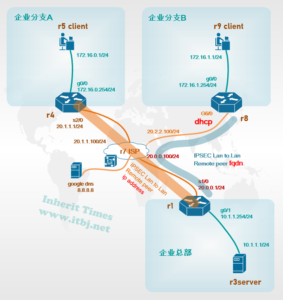
需求: 企业总部与各分支机构均已通过H3C 路由器接入互联网,为实现资源共享,同时保证数据安全,各分支至总部数据需通过IPSEC VPN加密
总部与分支A互联网出口均为固定IP
分支B互联网出口IP通过DHCP 动态获取
总部r1配置:
[r1]dis current-configuration
#
sysname r1
#
interface Serial1/0
ip address 20.0.0.1 255.255.255.0
nat outbound name snat
ipsec apply policy allpeermap
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 10.1.1.254 255.255.255.0
#
ip route-static 0.0.0.0 0 20.0.0.100
#
acl advanced name r4ipsec
rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.0.0 0.0.0.255
#
acl advanced name r8ipsec
rule 10 permit ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
#
acl advanced name snat
rule 1 deny ip source 10.1.1.0 0.0.0.255 destination 172.16.0.0 0.0.0.255
rule 2 deny ip source 10.1.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
rule 10 permit ip source 10.1.1.0 0.0.0.255
#
ipsec transform-set allpeer
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2
#
ipsec policy-template pt 10
transform-set allpeer
security acl name r8ipsec
ike-profile r8ikepro
#
ipsec policy-template pt 11
transform-set allpeer
security acl name r4ipsec
local-address 20.0.0.1
remote-address 20.1.1.1
ike-profile r4ikepro
#
ipsec policy allpeermap 10 isakmp template pt
#
ike identity fqdn r1
#
ike profile r4ikepro
keychain r4
exchange-mode aggressive
local-identity address 20.0.0.1
match remote identity address 20.1.1.1 255.255.255.255
proposal 10
#
ike profile r8ikepro
keychain r8
exchange-mode aggressive
local-identity fqdn r1
match remote identity fqdn r8
proposal 10
#
ike proposal 10
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain r4
pre-shared-key address 20.1.1.1 255.255.255.255 key simple 123456
ike keychain r8
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123456
#
return分支A r4配置:
[r4]display current-configuration
#
sysname r4
#
interface Serial2/0
ip address 20.1.1.1 255.255.255.0
nat outbound name snat
ipsec apply policy r1map
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 172.16.0.254 255.255.255.0
#
ip route-static 0.0.0.0 0 20.1.1.100
#
acl advanced name r1ipsec
rule 10 permit ip source 172.16.0.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
acl advanced name snat
rule 1 deny ip source 172.16.0.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 10 permit ip source 172.16.0.0 0.0.0.255
#
ipsec transform-set r1peer
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2
#
ipsec policy r1map 10 isakmp
transform-set r1peer
security acl name r1ipsec aggregation
local-address 20.1.1.1
remote-address 20.0.0.1
ike-profile r1ikepro
#
ike profile r1ikepro
keychain r1
exchange-mode aggressive
local-identity address 20.1.1.1
match remote identity address 20.0.0.1 255.255.255.255
proposal 10
#
ike proposal 10
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain r1
pre-shared-key address 20.0.0.1 255.255.255.255 key simple 123456
#
return分支B r8配置
[r8]display current-configuration
#
sysname r8
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 172.16.1.254 255.255.255.0
#
interface GigabitEthernet6/0
port link-mode route
combo enable copper
ip address dhcp-alloc
nat outbound name snat
ipsec apply policy r1map
#
acl advanced name r1ipsec
rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
acl advanced name snat
rule 1 deny ip source 172.16.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
rule 10 permit ip source 172.16.1.0 0.0.0.255
#
ipsec transform-set r1peer
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
pfs dh-group2
#
ipsec policy r1map 10 isakmp
transform-set r1peer
security acl name r1ipsec
remote-address 20.0.0.1
ike-profile r1ikepro
#
ike identity fqdn r8
#
ike profile r1ikepro
keychain r1
exchange-mode aggressive
local-identity fqdn r8
match remote identity fqdn r1
proposal 10
#
ike proposal 10
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike keychain r1
pre-shared-key address 20.0.0.1 255.255.255.255 key simple 1234576
#
return验证测试:
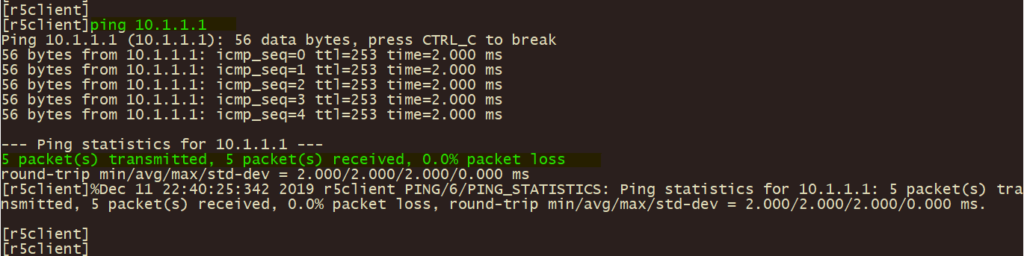
1、分支客户端ping 总部服务器地址 10.1.1.1,测试IPSEC VPN 联通性;
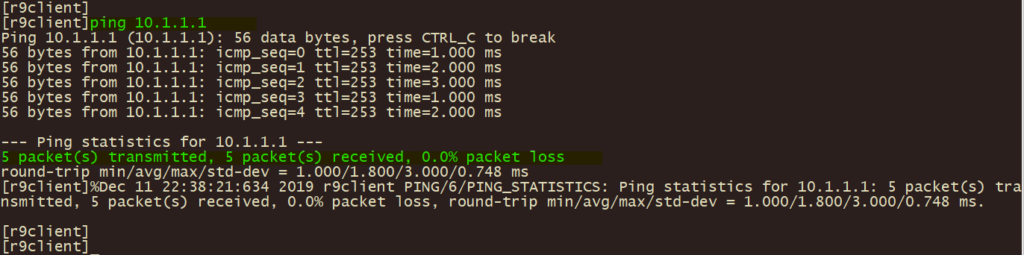
2、分支r4\r8 使用 display ike sa , display ipsec sa , display ipsec tunnel , 验证IPSEC VPN 第一阶段、第二阶段协调状态及IPSEC隧道状态;
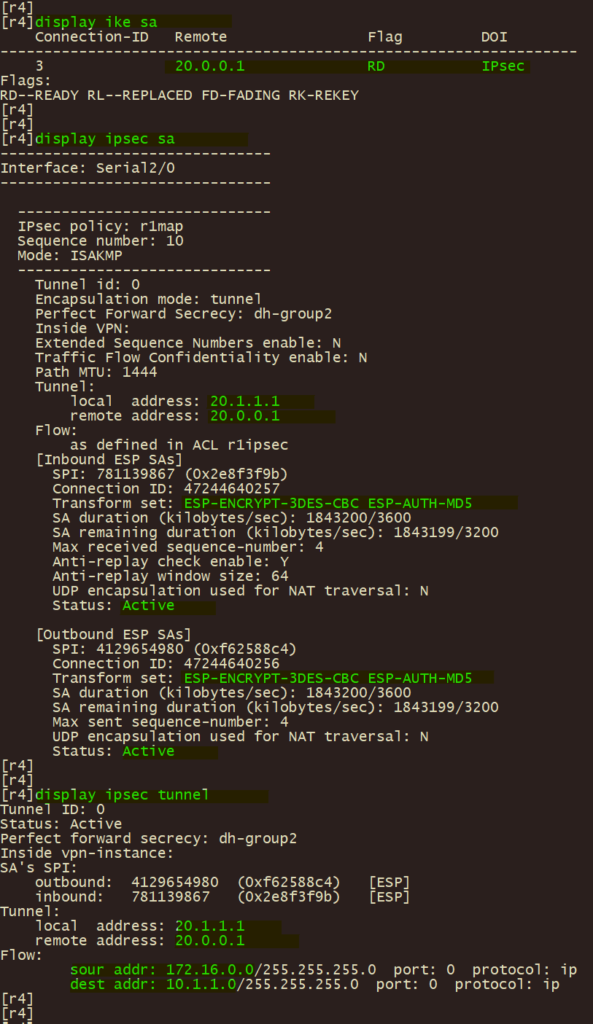
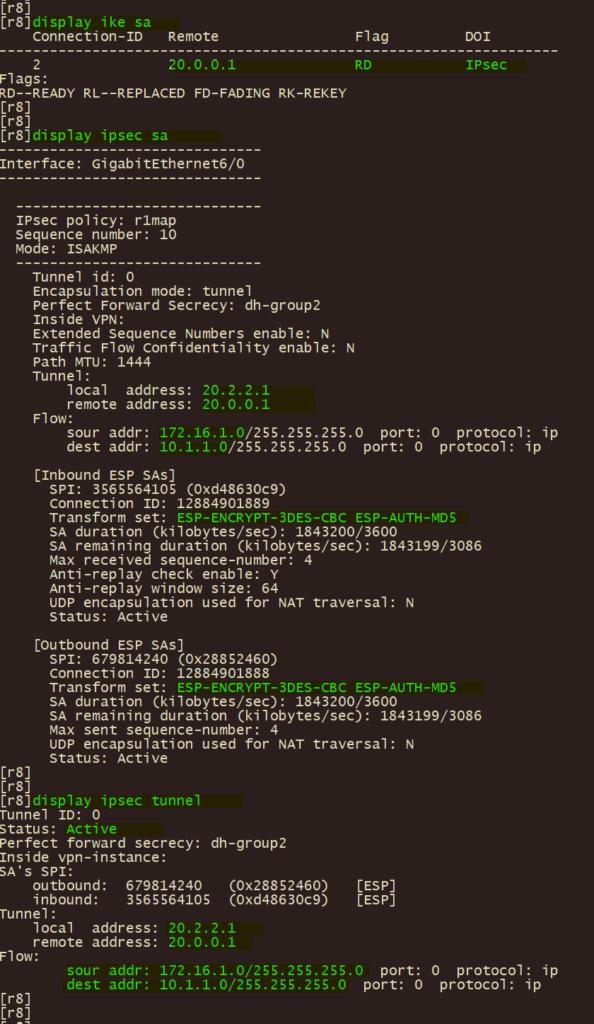
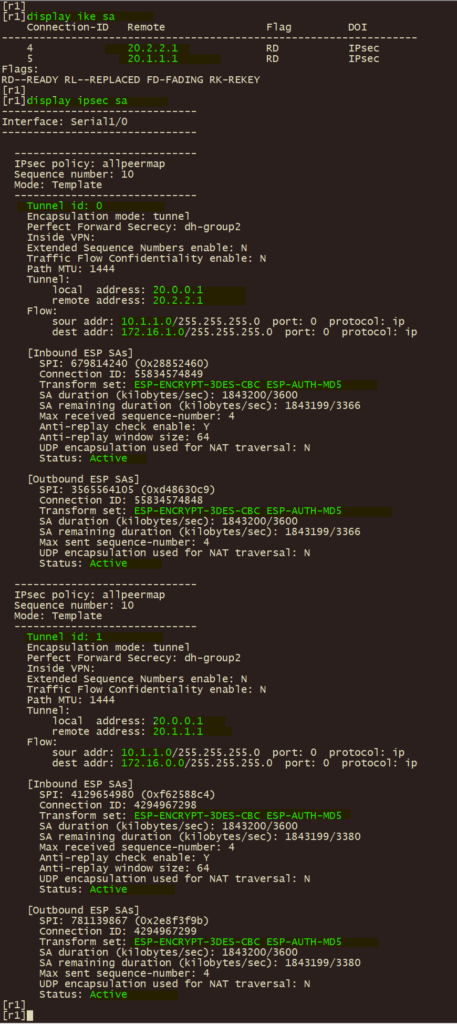
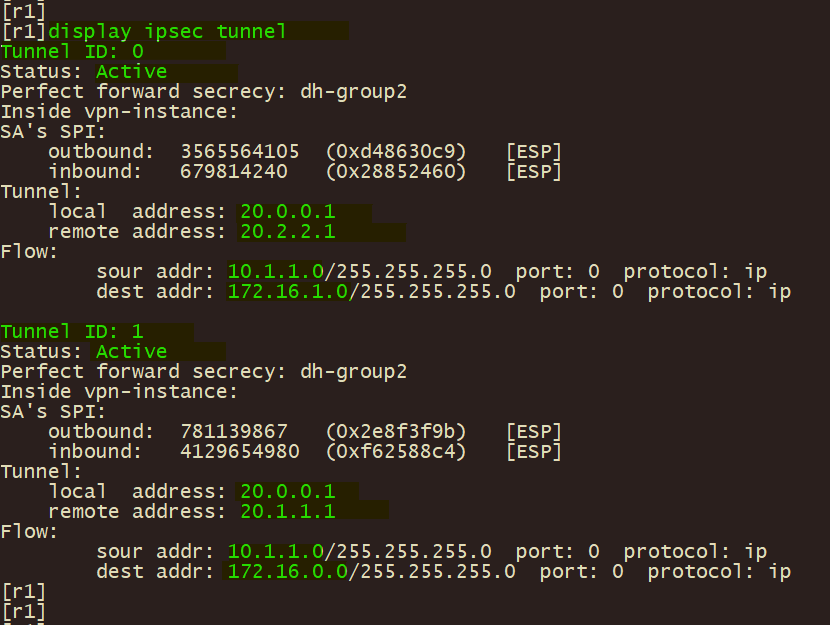
3、总部 r1 使用 display ike sa , display ipsec sa , display ipsec tunnel , 验证IPSEC VPN 第一阶段、第二阶段协调状态及IPSEC隧道状态。