需求:
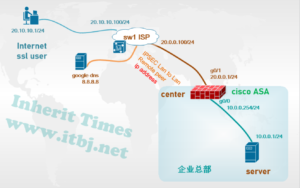
企业总部部署CISCO ASA 做为互联网出口网关,对外部提供ssl vpn服务以使用远程移动办公人员可接入企业内网,访问内部资源。
CISCO ASA SSL配置:
center# show running-config
: Hardware: ASA5550, 1024 MB RAM, CPU Pentium 4 3000 MHz
:
ASA Version 9.1(7)32
!
hostname center
ip local pool inheritssluser 10.100.1.1-10.100.1.200 mask 255.255.255.0
!
interface GigabitEthernet0/0
nameif inside
security-level 100
ip address 10.0.0.254 255.255.255.0
!
interface GigabitEthernet0/1
nameif outside
security-level 0
ip address 20.0.0.1 255.255.255.0
!
object network obj-10.0.0.0
subnet 10.0.0.0 255.255.255.0
object network obj-ssluser
subnet 0.0.0.0 0.0.0.0
access-list trust extended permit icmp any4 any4
access-list untrust extended permit icmp any any
access-list splittunnel extended permit ip 10.0.0.0 255.255.255.0 10.100.1.0 255.255.255.0
nat (inside,outside) source static obj-10.0.0.0 obj-10.0.0.0 destination static obj-ssluser obj-ssluser
!
object network obj-10.0.0.0
nat (inside,outside) dynamic interface
access-group untrust in interface outside
route outside 0.0.0.0 0.0.0.0 20.0.0.100 1
crypto key generate rsa label inheritssl
crypto ca trustpoint inherittrust
enrollment self
fqdn 20.0.0.1
enrollment self
subject-name CN=20.0.0.1
crl configure
keypair inheritssl
crypto ca enroll inherittrust noconfirm
ssl trust-point inherittrust outside
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-4.7.04056-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
group-policy inherit internal
group-policy inherit attributes
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value splittunnel
default-domain value itbj.net
address-pools value inheritssluser
username ssluser1 password 123456
username ssluser1 attributes
vpn-group-policy inherit
vpn-simultaneous-logins 100
tunnel-group inherittimes type remote-access
tunnel-group inherittimes general-attributes
default-group-policy inherit
tunnel-group inherittimes webvpn-attributes
group-alias itbj.net enable
!
: end
asa5550# SSL VPN用户PC端配置验证:
1、浏览器访问 https://20.0.0.1
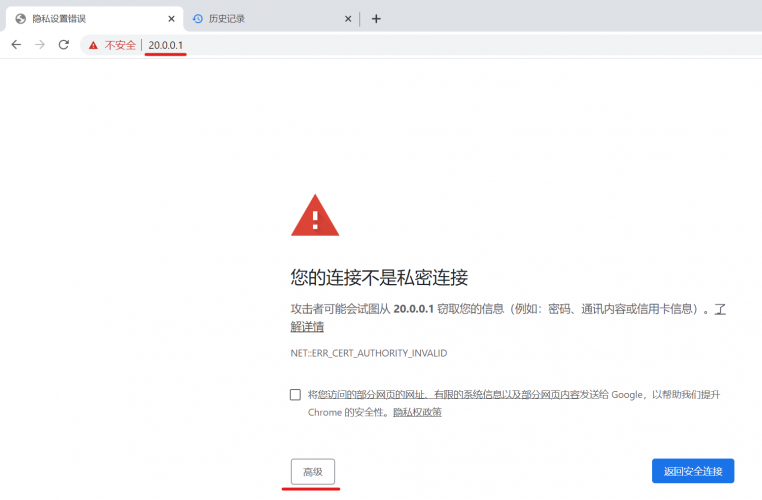
2、输入用户名/密码;
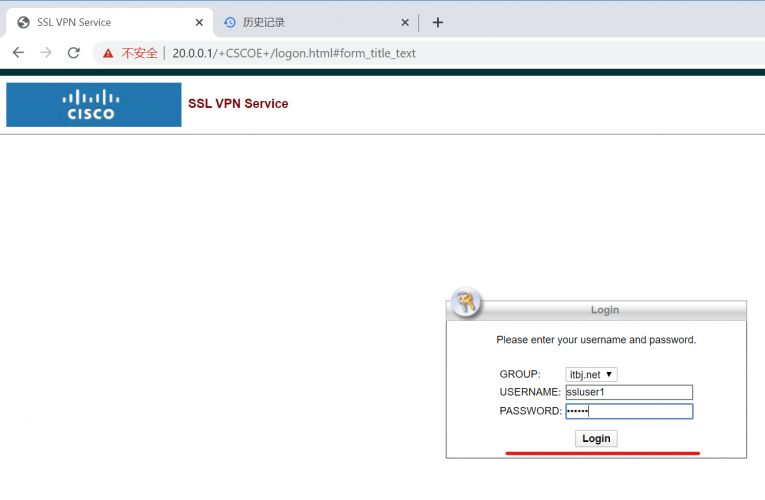
3、下载windows客户端;
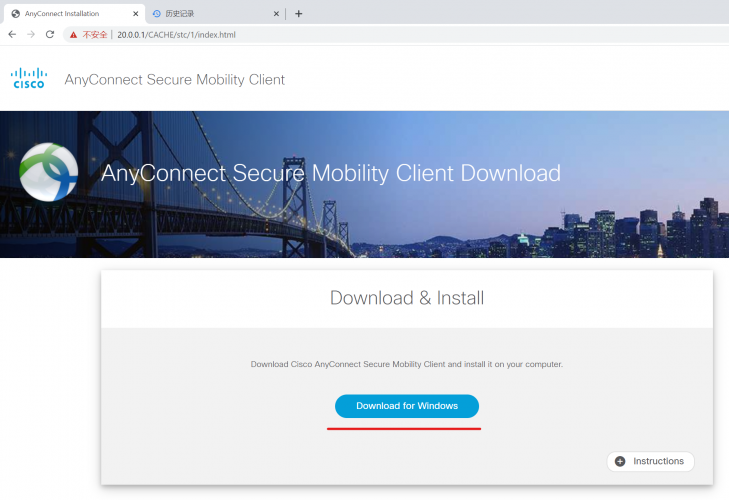
4、安装 anyconnect for windows客户端;
5、开启 anyconnect 客户端;
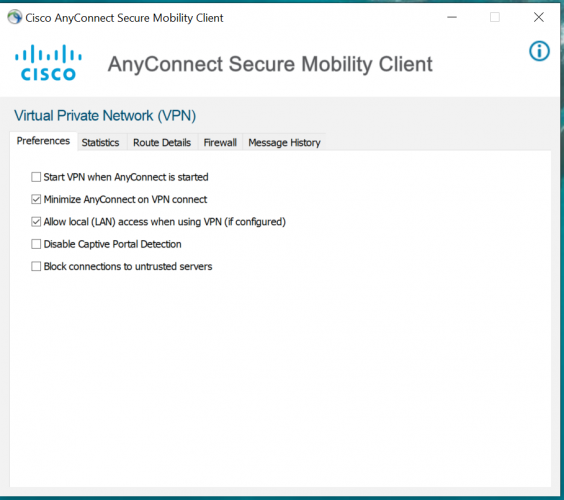
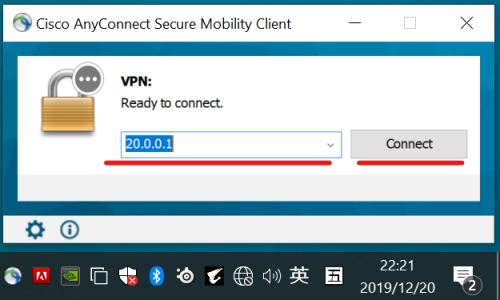
6、输入ssl vpn 服务器地址并按图设置连接选项后点击连接;
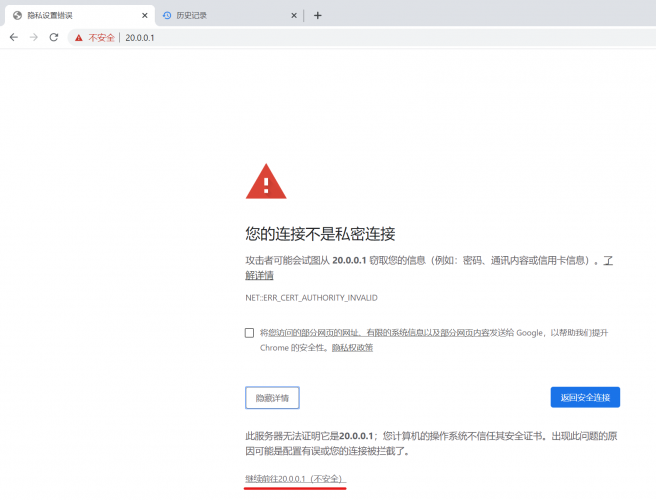
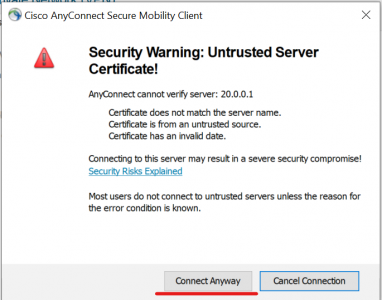
7、按图选择继续连接;
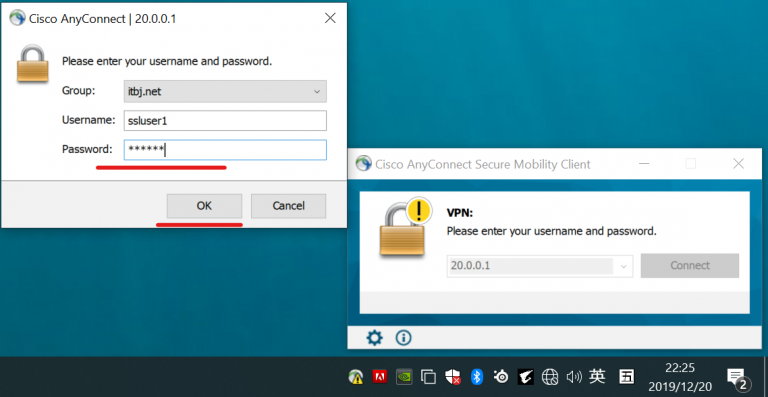
8、输入用户名/密码后点击ok按钮,ssl vpn服务器开始对用户进行认证;
10、检查、验证 vpn连接状态,查看隧道分离路由;
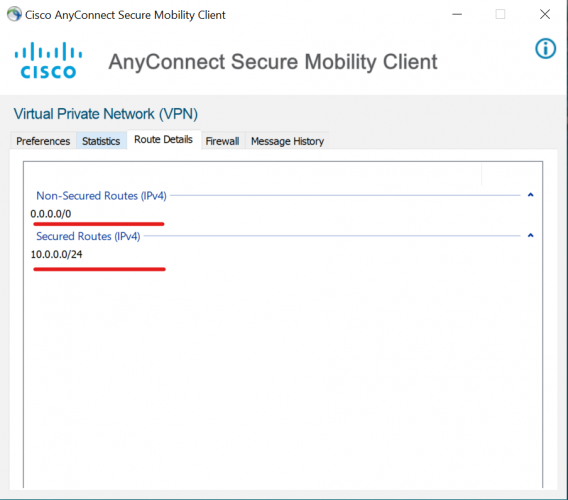
11、pc 客户端 ping 总部服务器地址和公网地址,验证ssl vpn 可用性;